One of the biggest divisions in blockchain technology is permissioned versus permissionless blockchains. The basic distinction is pretty clear: you need approval to use a permissioned blockchain, while anyone can participate in permissionless systems. The original Bitcoin blockchain was and is still completely open, for example, but as companies and institutions start to adopt the technology, they’re willing to sacrifice trustlessness and transparency for better access controls and easier customization.
Why do we care? As similar as the two systems might sound, they really shouldn’t be used for the same things. People probably won’t be so keen on using a permissioned cryptocurrency, for example, since one of the biggest draws of crypto is that no one can control how it works or where it goes. Conversely, a company like Maersk, which uses blockchain to track its shipping logistics, doesn’t want to put all of its confidential data onto a permissionless blockchain.
How permissioned and permissionless blockchains are similar
Both permissioned and permissionless blockchains have some important characteristics in common:
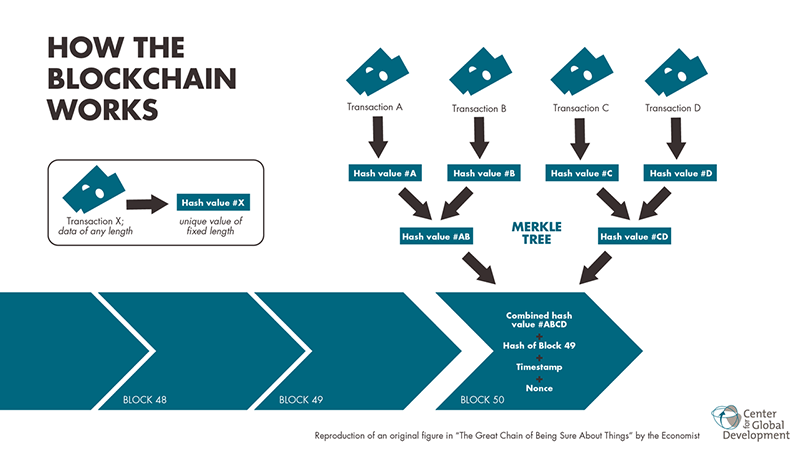
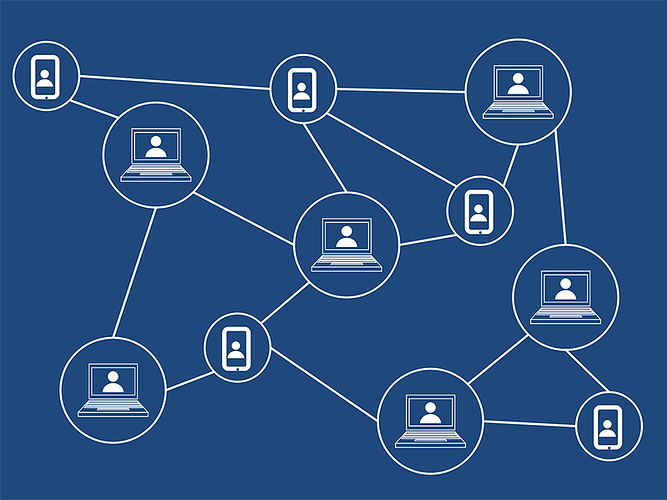
- They’re both distributed ledgers, meaning that there are multiple versions of the same data stored in different places and connected through some type of network.
- They both use some form of consensus mechanism, which means they have a way for multiple versions of the ledger to reach an agreement on what they should all actually look like.
- They are both theoretically immutable in the sense that the data they store can’t be changed without having sufficient power over the network. Even then, the blocks are linked by cryptographic hashes that will change if any data is altered.
Put simply, both permissioned and permissionless blockchains use cryptography and decentralization to varying degrees to accurately store data in a format that is difficult to hack or alter.
Permissionless blockchains
Most of the blockchains you’ve probably heard of fall into this category: Bitcoin, Ethereum, Litecoin, Dash, and Monero. All the others are public blockchains that anyone can transact on or even join as a validator.
All the data stored on these chains is publicly available, and full copies of the ledgers are stored all around the world, which is what makes these systems very hard to hack or censor. No one runs the blockchain, no one can restrict access to it, and you can remain relatively anonymous since you don’t need to identify yourself to get an address and perform transactions.
This type of blockchain tends to generate buzz since it’s what underlies most cryptocurrencies and the most exciting decentralization solutions. The hype is deserved, since permissionless public blockchains can potentially revolutionize services that previously required trusted middlemen – not just currency. An immutable blockchain of cars could give you the ability to look up reliable data on every part, service record, and transaction associated with a used car instead of trusting the guy on Craigslist, for example.
Of course, this system is far from perfect. It can be slow, difficult to build for and scale up on, too transparent to keep sensitive data on, hard to control access to, energy-intensive, and complex. That’s why permissioned blockchains are becoming a more popular solution for companies and institutions looking to use blockchains to replace more traditional systems.
Permissioned blockchains
In a nutshell, permissioned blockchains are only open to those who are allowed access. Anyone who wants to validate transactions and/or view data on the network has to be approved by the central authority first.
This is especially useful for banks, companies, and other institutions that have to comply with regulations and might not be fans of losing complete control of their data. Instead of building on a large, decentralized blockchain like Ethereum, they can instead create a custom solution run only by institutions that they approve of.
Imagine a watermelon company taking their supply chain to the next level:
- The company decides to build a blockchain system to track its delicious fruit from farm to store. They need to ensure that nobody slips in any subpar watermelons and want to know exactly who is involved in each step, so they decide on a permissioned blockchain that only authorized users can access.
- They build a Melonchain and give each stop on their supply chain a way to access it and add data, which is validated by a network of servers run by the company. This way, whenever data about a melon is logged, it can be looked up in the ledger and cryptographically verified later.
- Certain data about each watermelon, like harvest date and location, is made public for consumers, while other data, like exact movements along the supply chain, are kept confidential to help the company retain its competitive edge.
Facebook’s Libra cryptocurrency is another good example. It might go fully public in the future, but at the time of its launch, only a select number of companies that have invested and been approved will be allowed to operate it, and users may have to sign up with real identities.
The big advantages of permissioned blockchains are that they have:
- Access controls
- High customizability
- An easier time changing to comply with regulations
- Better energy-efficiency
- Potentially better scalability
There are disadvantages, too, however. They are:
- More centralized
- Less transparent
- More vulnerable to hacks and manipulation
- More easily censored
- Less anonymous
Which one is better?
Permissionless and permissioned blockchains are just branches of the same technology that have developed in response to different needs. Both of them are useful in their own way, and are, for most practical purposes, different technologies.
This means that the benefits brought by a permissionless blockchain don’t map directly over to permissioned systems, so just because a company says it’s using blockchain technology doesn’t necessarily mean it’s that much more private or decentralized than a traditional database. The permissioned-permissionless distinction is where the buzzword really starts to break down, making it a pretty important piece of the puzzle to know.






 !
!