1. Surface Web:
The Surface net is that the portion of the globe Wide net that’s without delay obtainable to the overall public and searchable with customary net search engines
The Surface net solely consists of ten % of the data that’s on the web. The Surface net is formed with a group of static pages. These ar web content that are in a very server, available to be accessed by any search engine.
2. Deep Web :
The Deep net refers to any web site that can’t be without delay accessed through any standard computer program like Google or Yahoo! Search.
The reason for this can be as a result of the content has not been indexed by the computer program in question.
3. Dark Web :
This corner of the web lies inside the deepest points of the web chasm.
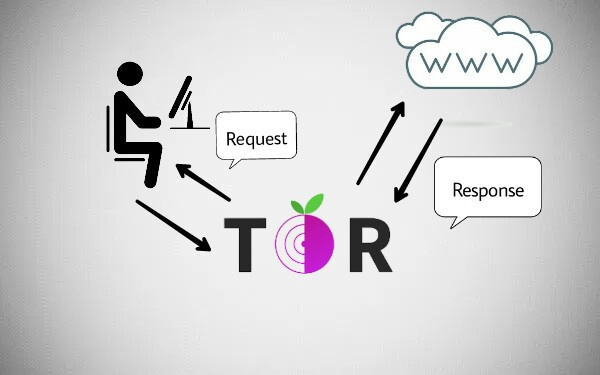
Dark World guests usually utilize specialized namelessness code like Tor to mask their identity. Traditionally, once internet} user visits any web site that exists on the globe wide web, they’re tracked via their net Protocol (IP) address.
Surfing the Dark net is a wholly totally different matter altogether, with masking code accustomed render a private laptop anonymous whereas masking identity, location, IP address, and more.
So here is the brief summary of Tor , Dark Web and a Deep Web . Lets come to installation and their precautions.
When the program is placed in, you’ll require a noticeable late envelope alluded to as Tor Browser . Open it and you’ll see “Begin Tor Browser .exe”.
Click that document and another window opens requesting that whether you’d like interface straightforwardly to the Tor organize or on the off chance that you have to design intermediary settings first.
To ensure you’re associated with Tor go to whatismyip.com, which will naturally distinguish your area dependent on your Internet Protocol address.
On the off chance that your program demonstrates you originating from an area that isn’t your own, you are ready.
Simply ensure you do all your mysterious perusing from the Tor Browser itself as different projects on your framework are not associated with Tor.
For the vast majority, picking the immediate alternative is ideal, so pick Connect.
A couple of moments later a form of Firefox will dispatch and you are presently associated with the Tor system and ready to program in relative namelessness.
Be that as it may, perusing namelessly on Tor isn’t exactly as simple as booting up a program.
There are likewise a few principles of the street you ought to watch, for example, interfacing with each site conceivable by means of SSL/TSL encryption (HTTPS) . In the event that you don’t, at that point anything you do online can be seen by the individual running your leave hub.
The program has the Electronic Frontier Foundation’s HTTPS everyplace add-on put in as a matter of course, that should cowl your SSL/TSL wants more often than not.
Likewise, remember that perusing in lack of definition doesn’t make you impervious to infections and distinctive malware.
In case you’re getting to the seedier parts of the web, Tor can’t shield you from pernicious programming that could be utilized to uncover your area.
For the normal net client, be that as it may, the Tor Browser should be sufficient to stay individual on-line.
Things you shouldn’t do while utilizing Tor:
-
Try not to utilize your cell phone for a 2-Step check on Tor
-
Try not to work client accounts outside TOR
-
Try not to post your own data.
-
Try not to send decoded information over TOR
-
Keep in mind to erase treats and neighbourhood site information
-
Try not to utilize TOR for Google Search.
-
Try not to utilize HTTP site on TOR
-
Try not to interface with a similar server with and without TOR at the same time.


 !
!