Nikto is a very fashionable and simple to make use of webserver evaluation software to search out potential issues and vulnerabilities in a short time. This tutorial exhibits you the right way to scan webservers for vulnerabilities utilizing Nikto in Kali Linux. Nikto comes commonplace as a software with Kali Linux and ought to be your first selection when pen testing webservers and net functions. Nikto is scanning for 6700 probably harmful recordsdata/packages, checks for outdated variations of over 1250 servers, and model particular issues on over 270 servers in accordance with the official Nikto website. You ought to know that Nikto isn’t designed as a stealthy software and scans the goal within the quickest means potential which makes the scanning course of very apparent within the log recordsdata of an intrusion detection methods (IDS).
Scanning Webservers with Nikto for vulnerabilities
These are a number of the main options within the present model:
- SSL Support (Unix with OpenSSL or perhaps Windows with ActiveState’s
Perl/NetSSL) - Full HTTP proxy help
- Checks for outdated server parts
- Save experiences in plain textual content, XML, HTML, NBE or CSV
- Template engine to simply customise experiences
- Scan a number of ports on a server, or a number of servers through enter file (together with nmap output)
- LibWhisker’s IDS encoding strategies
- Easily up to date through command line
- Identifies put in software program through headers, favicons and recordsdata
- Host authentication with Basic and NTLM
- Subdomain guessing
- Apache and cgiwrap username enumeration
- Mutation strategies to “fish” for content material on net servers
- Scan tuning to incorporate or exclude total courses of vulnerability
checks - Guess credentials for authorization realms (together with many default id/pw combos)
- Authorization guessing handles any listing, not simply the foundation
listing - Enhanced false optimistic discount through a number of strategies: headers,
web page content material, and content material hashing - Reports “unusual” headers seen
- Interactive standing, pause and modifications to verbosity settings
- Save full request/response for optimistic checks
- Replay saved optimistic requests
- Maximum execution time per goal
- Auto-pause at a specified time
- Checks for widespread “parking” websites
- Logging to Metasploit
- Thorough documentation
Another good characteristic in Nikto is the likelihood to outline the check utilizing the -Tuning parameter. This will allow you to run solely the checks you want which might prevent numerous time:
zero – File Upload
1 – Interesting File / Seen in logs
2 – Misconfiguration / Default File
three – Information Disclosure
four – Injection (XSS/Script/HTML)
5 – Remote File Retrieval – Inside Web Root
6 – Denial of Service
7 – Remote File Retrieval – Server Wide
eight – Command Execution / Remote Shell
9 – SQL Injection
a – Authentication Bypass
b – Software Identification
c – Remote Source Inclusion
x – Reverse Tuning Options (i.e., embrace all besides specified)
Nikto has it’s personal updating mechanism. We encourage you to verify for updates earlier than utilizing Nikto. Nikto will be up to date utilizing the next command:
nikto -update
Scanning webservers with Nikto
Let’s begin Nikto to scan for attention-grabbing recordsdata with choice 1 utilizing the next command:
nikto -host [hostname or IP]-Tuning 1
Please not which may be unlawful and punishable by legislation to scan hosts with out written permission. Do not use nikto on 1Hack.us however use Virtual machines for apply and check functions.
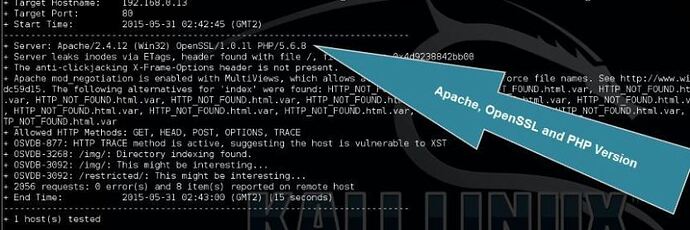
Nikto will now show the Apache, OpenSSL and PHP model of the focused webserver. Also it offers you an summary of potential vulnerabilities together with the Open Source Vulnerabilities Database (OSVDB) reference. When you search the OSVDB website for the reference code it should clarify the potential vulnerability in additional element. The OSVDB challenge presently covers greater than 120,980 vulnerabilities, spanning 198,973 merchandise from four,735 researchers, over 113 years.
Running all Nikto scans in opposition to a number
To run all scans in opposition to a specific host you should utilize the next command:
nikto -host [hostname or IP]
Running all scans will take numerous time to finish.
Running Nikto in opposition to a number of hosts
Password : EHT
Nikto gives a number of choices to check a number of hosts:
- By utilizing a sound hosts file containing one host per line
- Piping Nmap output to Nikto.
A legitimate host file is a textual content file containing the hosts, it’s a must to use one line for every host in an effort to make it legitimate for Nikto. Instead of utilizing the hostname as an argument for the -h choice you must use the filepath to the legitimate hosts file.
Another resolution is to pipe the Nmap output to Nikto. Nmap will output the legitimate hosts to Nikto and Nikto will run the chosen scans in opposition to these hosts. The following command will run a Nmap scan on host 192.168.zero.zero – 192.168.zero.24 utilizing a grepable output which is outlined by the -oG- flag:
nmap -p80 192.168.zero.zero/24 -oG – | nikto -h –
Please word that you must use a touch (-) for Nikto’s host choice to make use of the hosts provided by Nmap.!
 !
!