MITM Is anybody there who knows anything about this? The majority of the site reveals to you How to do MITM in HTTP sites. am I correct? However, In this instructional exercise, You will figure out How to do Man In the Middle Attack on HTTPS and How Hacker sniff your own data like username , secret passwords , and so forth regardless of you are utilizing a high-security type site.
The greater part of the general population ask me, How to do the assault on HTTPS sites? There are numerous tools of MITM which can change over an HTTPS demand into the HTTP and after that sniff the credentials. Numerous sites utilizing HSTS on their sites.
Basically HSTS is a kind of security which ensures sites against convention downsize assaults and treat seizing sorts of assaults. We can sidestep HSTS sites moreover.
Today, I will outline for you
- Man In The Middle Framework
- Introduce MITMF tool in your Kali Linux?
- Bypass HSTS security websites?
- How to be sheltered from these kinds of Attacks?
Man In The Middle Framework
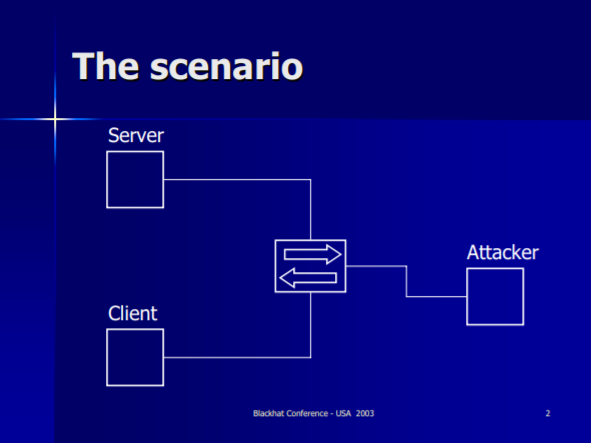
Its a sort of Attack which is done just on the private system. You can’t do this on Public Network. In this Attack, we set up MITMF in Kali.
Assume, an individual in a similar system surf Facebook.com then the parcel with a solicitation of facebook.com will go to the switch and afterward switch forward this solicitation to the Facebook server.
Be that as it may, If we set up MITMF in Kali then all the solicitation of the unfortunate casualty’s PC which is heading off to the switch. MITMF can catch these all parcels and can peruse the information from these bundles.
We can catch these all parcels utilizing M ITM F and can likewise observe what is composed on those bundles. In the event that someone login to their facebook account, at that point we are likewise ready to see the username and secret key of that facebook account.
This is a pre-downloaded tool in Kali. So, you have to install this tool by typing
apt-get install mitmf
After downloading MITMF, type
MITMF -h
MITMF-h command is used to see all the commands of this tool.
To perform this MITM attack for bypassing HSTS. You need some IP’s as given below.
Requirements:
Victim’s IP: You can find victim’s IP by netdiscover command.
Router IP: Also shown by the netdiscover command.
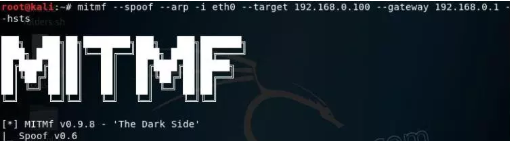
To start MITM type
mitmf –spoof –arp -i eth0 –target ‘ **target IP** ’ –gateway ‘ **router’s IP** ’ –hsts
After typing the upper command you will see that Man In The Middle Attack is start on the HSTS website also. To confirm this open your web browser and open facebook.com. Whenever you open facebook.com it opens Facebook with a different URL as it opens with webm.facebook.com with Not Secure.
Once your victim enters his/her email id and password then your mitmf will capture it.
HOW TO BE SAFE FROM MITM?
- Utilize Latest Operating Systems and Browsers
- Utilize a trusted network while filling your delicate subtleties
- Check SSL sign for every single site.
- Use Data Encryption type software.

 !
!