Hello Guys,
There are tons of blogs and resources available over the internet for helping you start your journey with Android Security Assessment but only a handful of resources which will explain in detail how to start with iOS Security Assessment. This blog aims at helping you start iOS Security Assessment.
Lab Setup
- You will need MacOS for source code analysis and debugging (it also makes black box testing easier).
- Unlike Android, Corellium is the only publicly available iOS emulator. The solution is paid and does not have a trial offer.
- And if you are not using the above method, then we will be needing a device for Dynamic Testing.
Jailbreak an iOS Device
- Visit Can I Jailbreak.
- Select the iOS version installed on the phone and follow the instructed steps.
- For me I had an iPhone 5s with iOS 12.4.8 as a testing device so I used unc0ver to jailbreak it.
Device Setup
-
Cydia
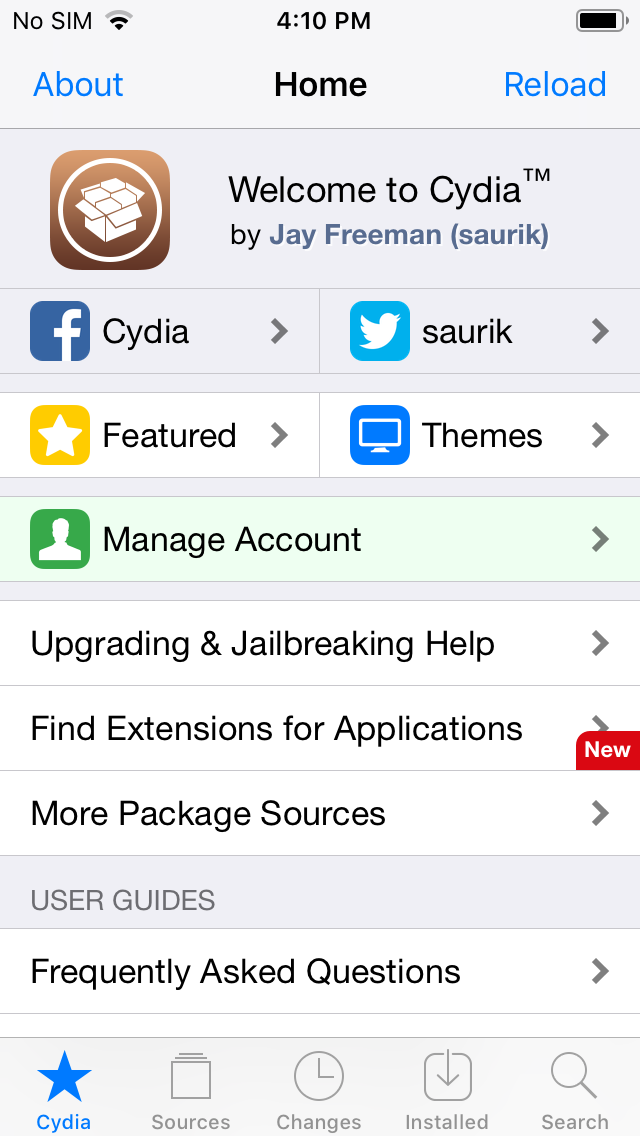
- Once jailbroken an iOS device you will find Cydia installed in it. It is a package manager for iOS. It enables a user to install applications and packages on a jailbroken iOS device. Most of the software packages available through Cydia are free, but some require purchasing.
- Once you have jailbroken the iOS device you will find “Cydia” installed in it by default.
- Once you open Cydia you will find 4 tabs on the footer.
- Sources
- Changes
- Installed
- Search
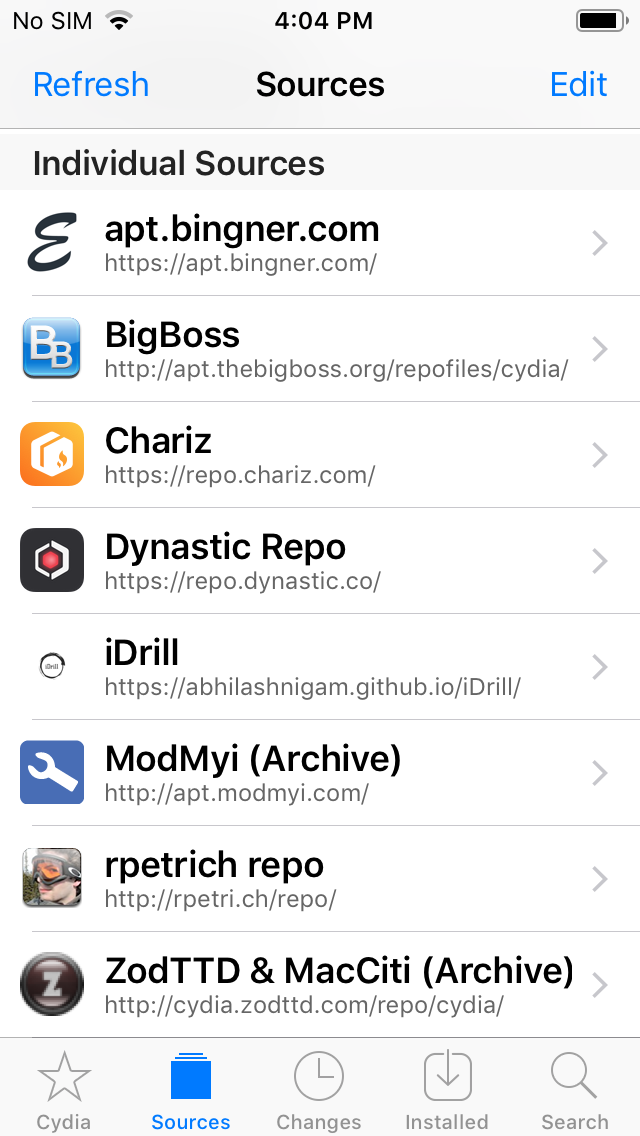
- “Sources” tab. These are all your pre-installed repository and where new sources will be added. Currently I have the below sources added. You can add different sources as per your needs.
- To add a source, click on “Edit” link in the top right and then click on the “Add” link. You will be presented a dialogue box like this.
- “Changes” and “Installed” tabs will tell you about all the packages installed and if any package needs to be updated.
- The “Search” tab is where you will find and install different packages from the different sources mentioned in the “Sources” tab.
-
The packages I usually install
- OpneSSH (if not pre-Installed)
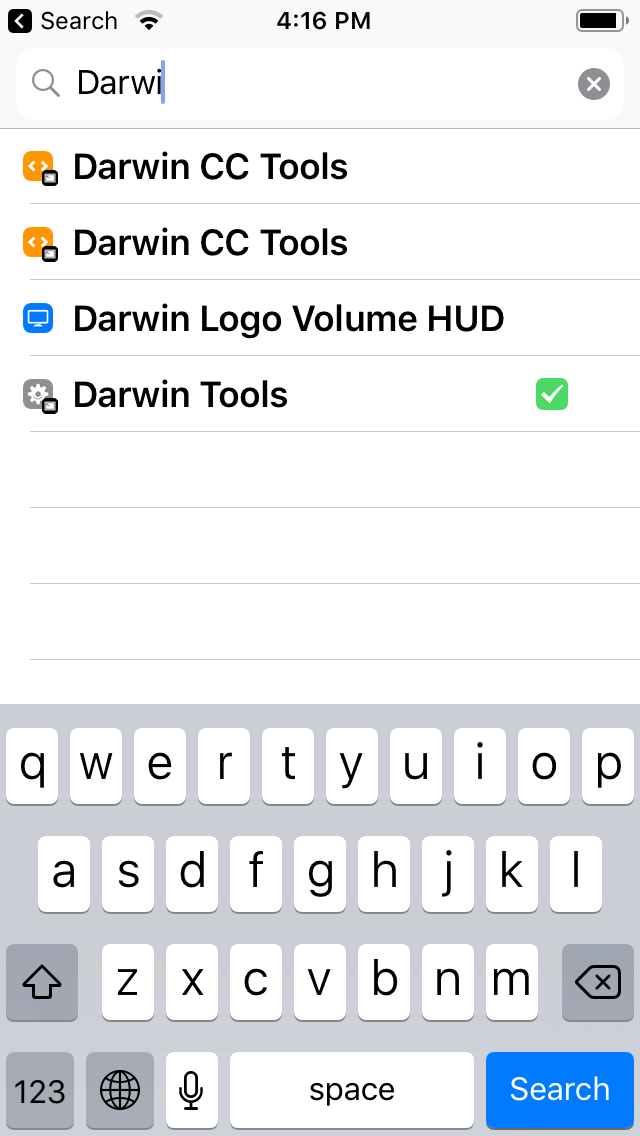
- Darwin CC Tools
- Filza File Manager
- Flex 3
- adv-cmds
- Keychain-Dumper
- IPA Installer
- Class-Dump
- Clutch 2
- iDrill
-
BurpSuite Proxy
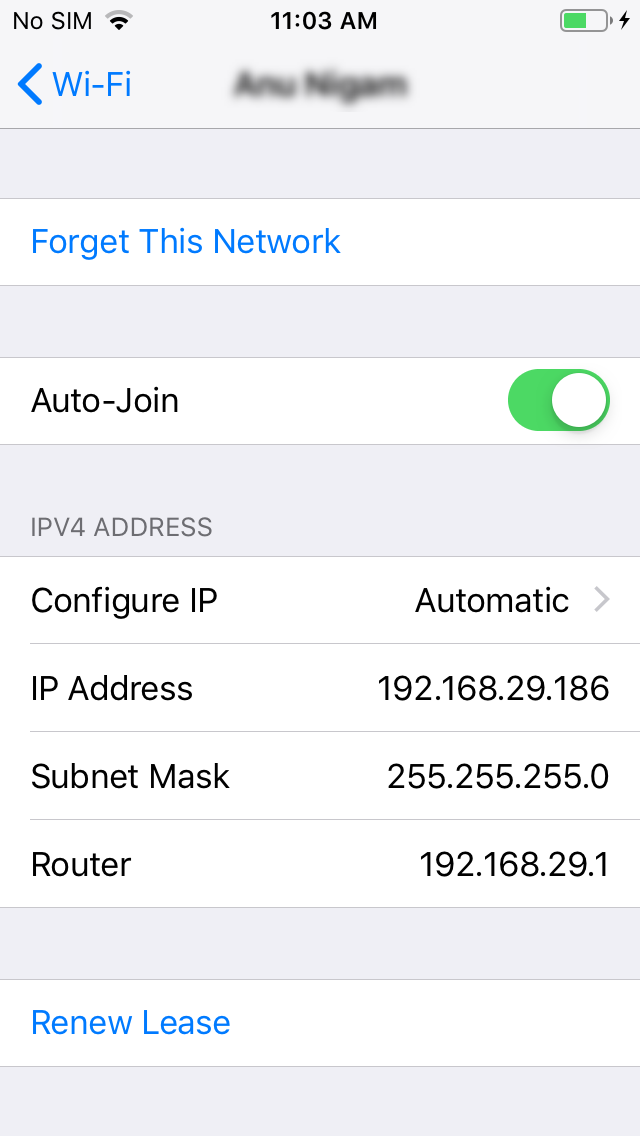
- Adding a Burp CA Cert to iOS device is simple. We need to start our BurpSuite listener on all interfaces or on a specific address which puts our BurpSuite listener on the same IP subnet. So, for me the iOS devices has IP address in 192.168.29.x subnet
- Now we need to start our BurpSuite listener on the same subnet or on all interfaces. We can do this by Starting Burp > Proxy Tab > Options Sub Tab > Selecting the running listener > clicking “Edit” button.

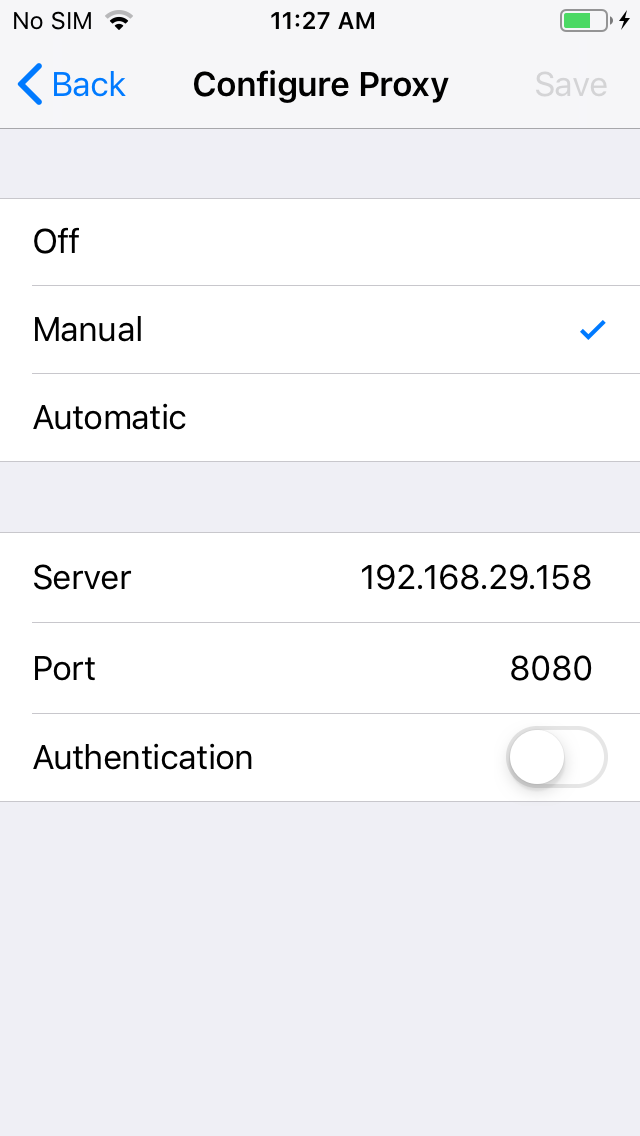
- We will now be adding our burp listener IP and Port as HTTP Proxy
- Once we have added out HTTP proxy, we need to download the Burp CA cert from http://burp so that we can surf HTTPS sites.
- Once we have the CA Cert downloaded, we will need to go to Settings > General > Profiles & Device Management and select PortSwigger CA. Click on the top right and follow the instructions to install the certificate.
- Adding a Burp CA Cert to iOS device is simple. We need to start our BurpSuite listener on all interfaces or on a specific address which puts our BurpSuite listener on the same IP subnet. So, for me the iOS devices has IP address in 192.168.29.x subnet
-
Flex3
- This tool helps you modify application code and behaviour, with no coding experience needed.
- Add “http://getdelta.co” source in Cydia or click here on your iOS device to automatically add source in Cydia.
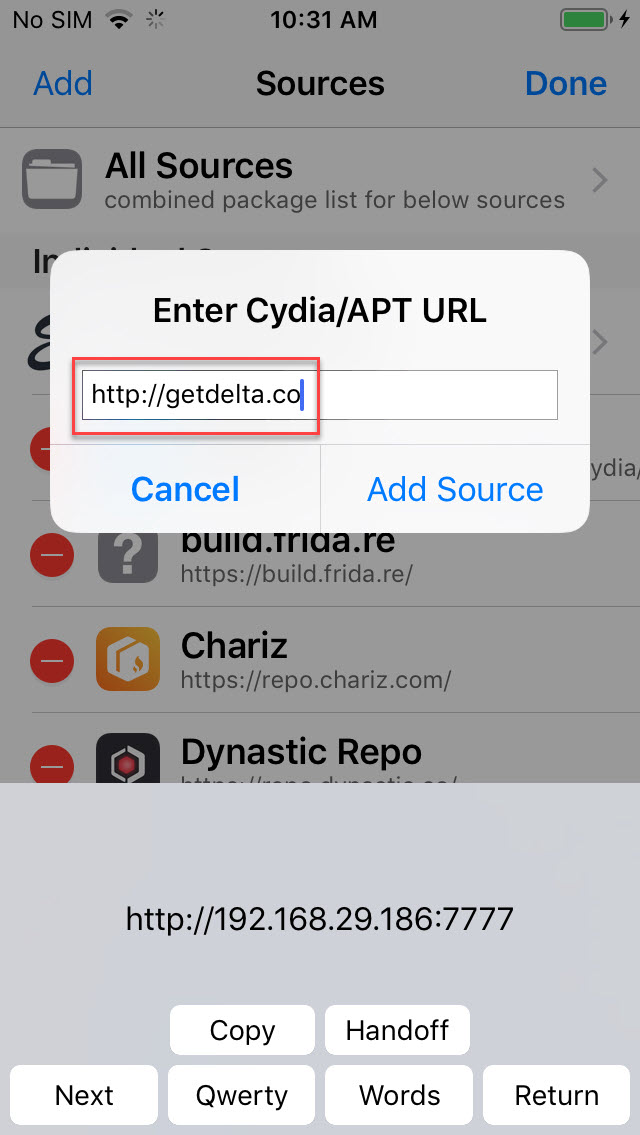
- Once added click on the Delta package > Tweaks > Select “Flex 3 Beta” package and install it

- You will now find the Flex icon on the Home.
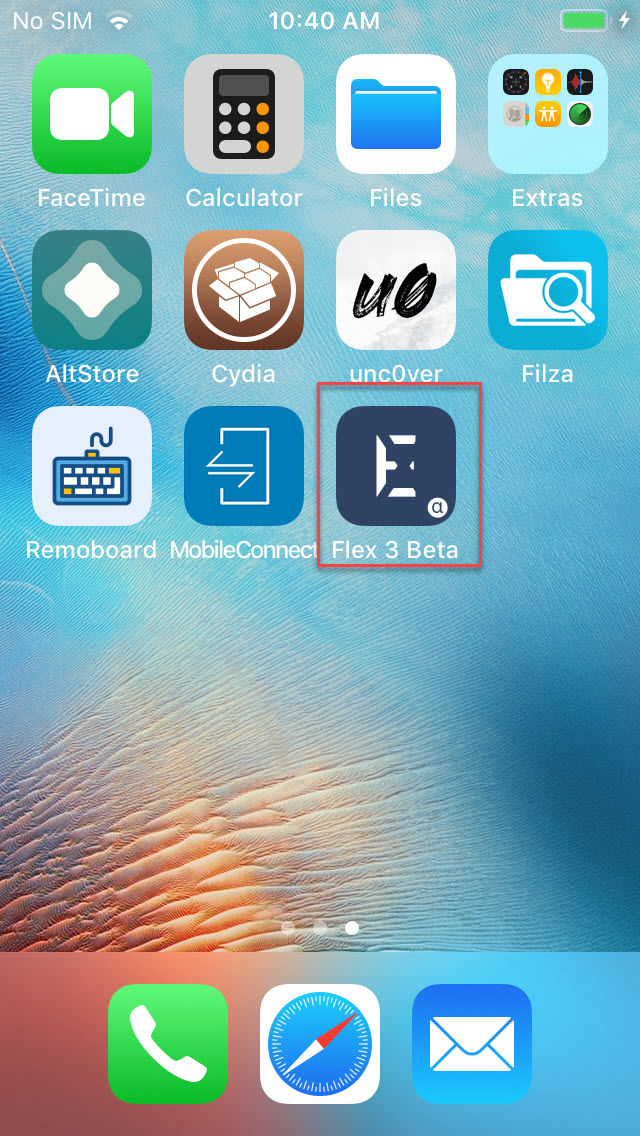
-
Keychain_dumper
- The tool allows a user to gain access to the stored key chains in the iOS device.
- To install it download the binary from here.
- Copy the “keychain_dumper” binary into the iOS device using the below command
scp keychain_dumper [email protected]:\usr\bin
- Then SSH into the iOS device and then run the command
keychain_dumperand observe the stored credentials.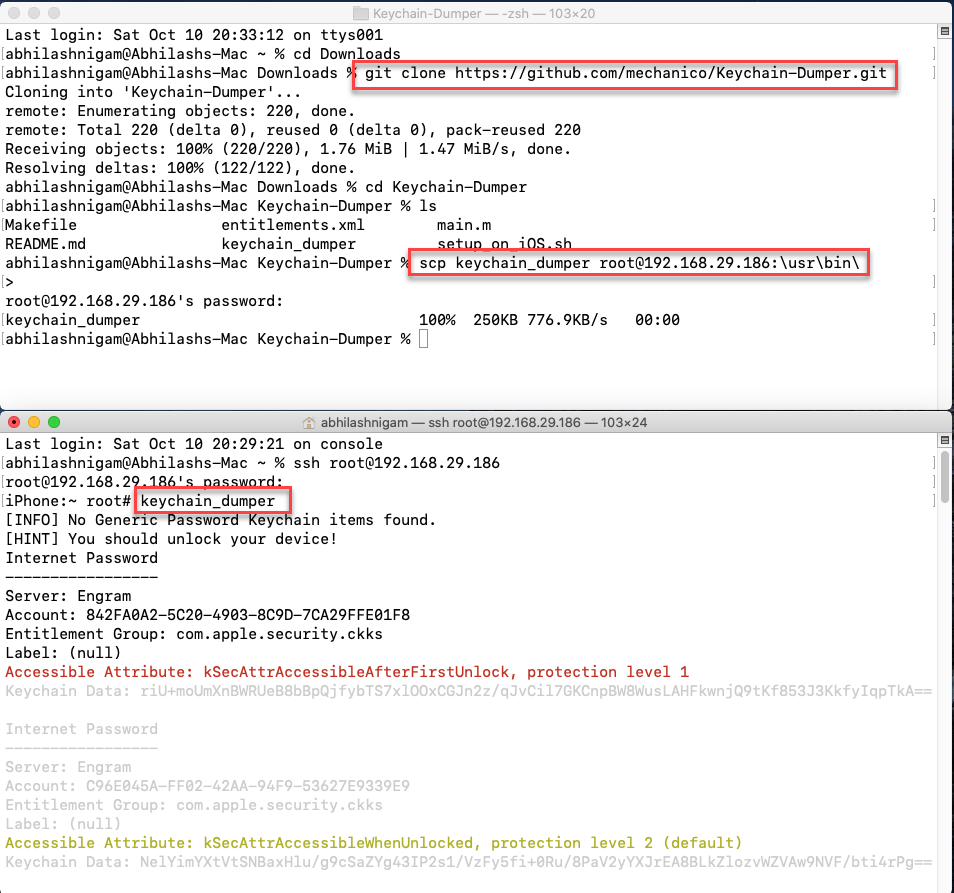
Machine Setup
-
For static testing of an iOS Application we prefer MacOS. If you have an Apple laptop good enough but for those who don’t have MacOS, they can use MacOS VM’s. There are tons of videos explaining in detail the setup of MacOS on VMWare or Virtual Box.
-
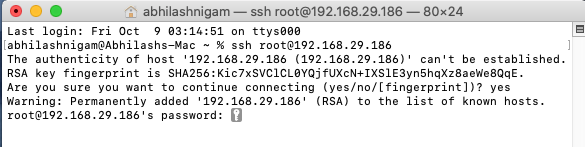
Once you have the MacOS setup running, it’s time to test the connection with the phone (this can be done on any other OS as well.)
-
Try and SSH into the machine as root. The default password is alpine.
-
We will now be setting up some tools for dynamic analysis. We will setup few of the tools
- Mobile-Security-Framework - MobSF
- Frida + Objection
- Keychain-Dumper
- Frida-ios-dump
-
Mobile-Security-Framework - MobSF
- MobSF is an automated, all-in-one mobile application pentesting framework that also supports iOS IPA files.
- To install it on MacOS you will need to download it on the Machine. The GitHub repository can be found here.
- The terminal installation can be done using the below commands.
# Prerequisites
Install Homebrew (ruby -e "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)")
Install Python (brew install python)
# Downloading and Installing the required packages
git clone https://github.com/MobSF/Mobile-Security-Framework-MobSF.git
cd Mobile-Security-Framework-MobSF
./setup.sh # For Linux and Mac
setup.bat # For Windows
# Running MobSF Server
./run.sh # For Linux and Mac
run.bat # For Windows
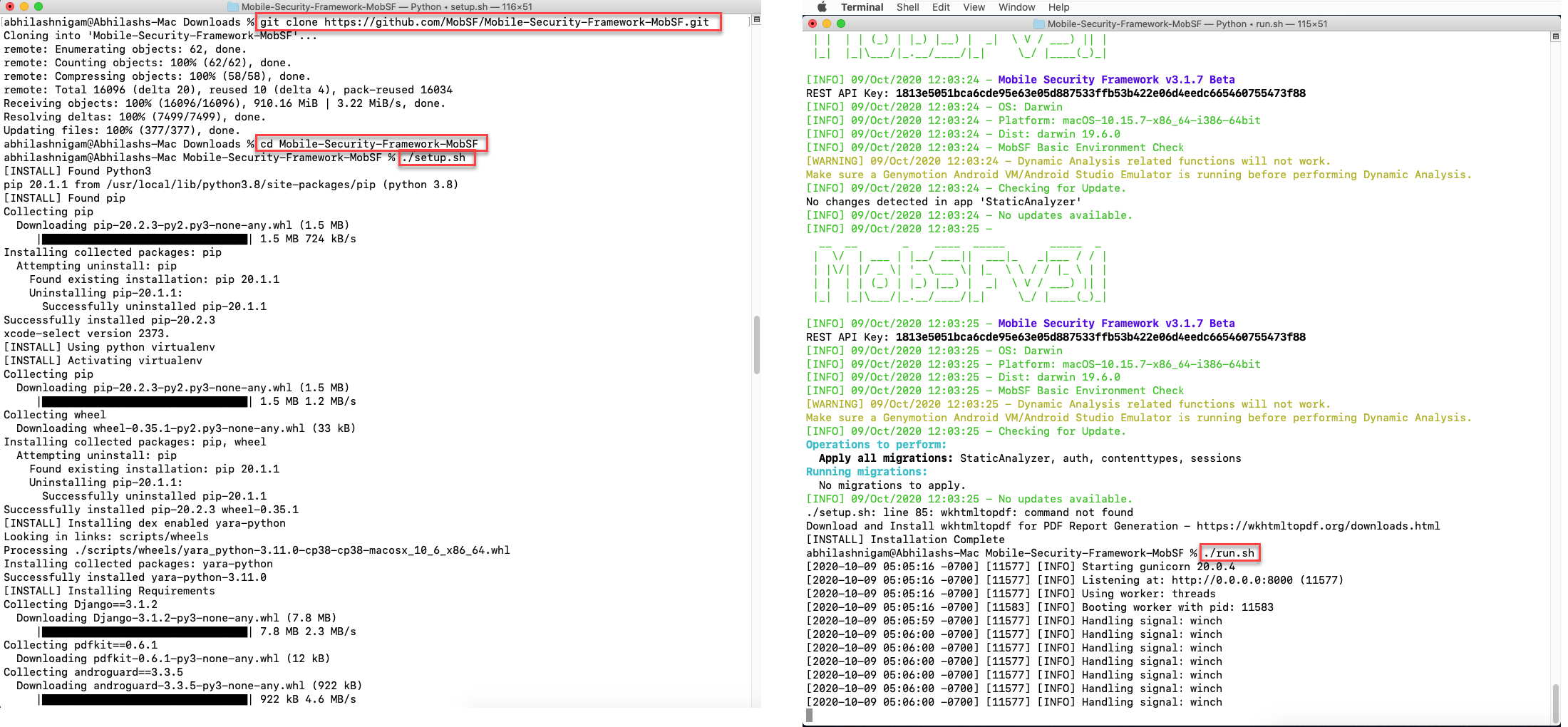
Once server is running you could navigate to http://127.0.0.1:8000 to access the MobSF GUI. Now simply drag the IPA you want to analyse into the upload area and MobSF will start its job.

-
Frida + Objection
- Frida lets you inject snippets of JavaScript or your own library into native apps on Windows, macOS, GNU/Linux, iOS, Android, and QNX.
- Objection is a runtime mobile exploration toolkit, powered by Frida, built to help you assess the security posture of your mobile applications, without needing a jailbreak.
- To install Frida and objection on MacOS we will need run the below commands
# Prerequisites
Install Homebrew (ruby -e "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)")
Install Python (brew install python)
# Downloading and Installing the required packages
pip3 install frida-tools
pip3 install objection
# Running Frida Client
frida-ps -U # to list the running application
objection --gadget "<package name>" explore
 We also need to install a Frida server on the iOS device. To install the Frida server on the follow the below steps
We also need to install a Frida server on the iOS device. To install the Frida server on the follow the below steps
# Prerequisites
Adding a source in cydia
Within Cydia, go to Sources > Edit > Add
https://build.frida.re
# Downloading and Installing the required packages
Then go to "Search" tab and search frida
Install frida suitable for your device.
# Running Frida Server
To run frida server SSH in to the iOS device
frida-server

-
Frida-ios-dump
- This tool allows us to extract .ipa for installed application.
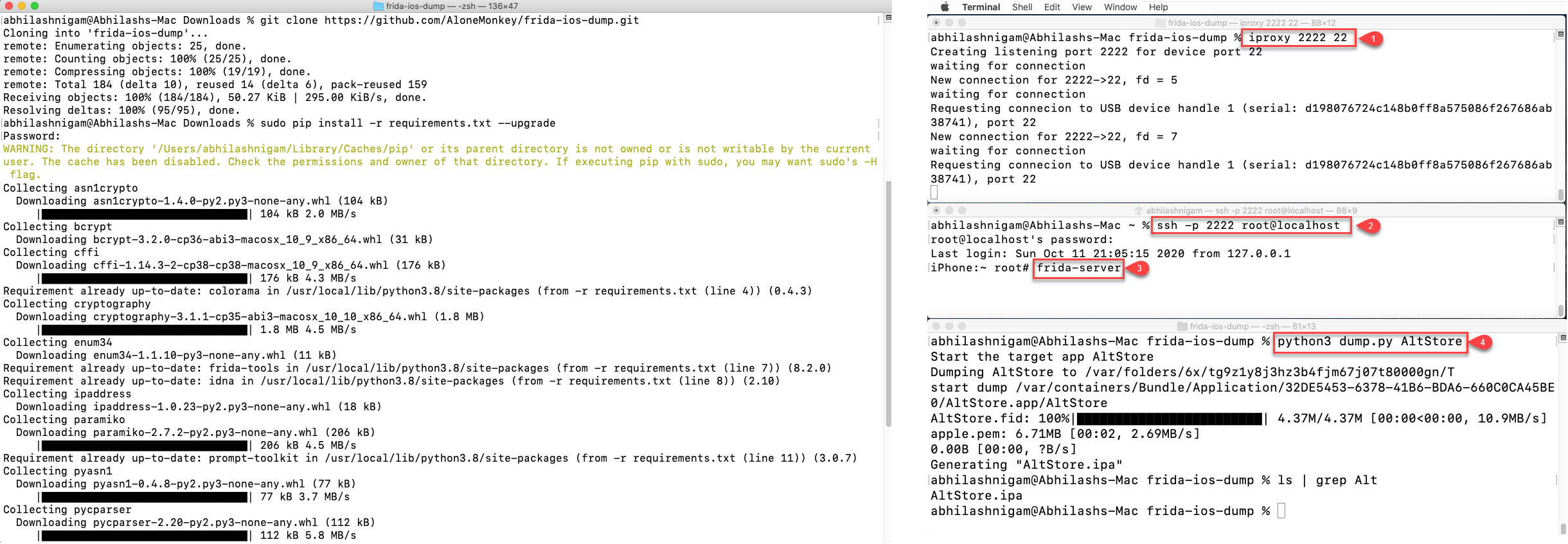
- You can download Frida-ios-dump from here. To install it follow the below steps
# Prerequisites
Install Homebrew (ruby -e "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)")
Install Python (brew install python)
# Downloading and Installing the required packages
git clone https://github.com/AloneMonkey/frida-ios-dump.git
cd frida-ios-dump
sudo pip install -r requirements.txt --upgrade
# Running Frida Client
iproxy 2222 22
ssh -p 2222 root@localhost (alpine as password)
Run frida server on iOS device
./dump.py <App Name>
 This concludes our blog. In the next blog we will be working on an iOS Application and we will see all the tools installed in action.
This concludes our blog. In the next blog we will be working on an iOS Application and we will see all the tools installed in action. (Source: payatu)
Happy learning!










 !
!