$5,005 worth vulnerability Duplicated, How I loose $5,005 in a day? Denial of Service - Billion LAUGH Attack (XXE)
OWASP Top 10 — XML External Entity
Hey everyone,
This is M. Asim Shahzad a.k.a protector47 , A Pakistani Cyber Security Researcher & passionate Bug Bounty Hunter.
As usual, I will try to describe my finding from scratch. I hope you guys will learn something new from this finding.
Prerequisites:
- What is XML(eXtensible Markup Language)?
- What is XML Parser?
- What is DoS(Denial of Service)?
- What is XML External Entity?
What is XML (eXtensible Markup Language)?
- XML (eXtensible Markup Language) is a markup language.
- XML is designed to store and transport data. XML was released in late ’90s. it was created to provide an easy to use and store self-describing data.
- XML became a W3C Recommendation on February 10, 1998.
- XML is not a replacement for HTML.
- XML is designed to be self-descriptive.
- XML is designed to carry data, not to display data.
- XML tags are not predefined. You must define your own tags.
- XML is platform-independent and language independent.
Reference: https://www.w3schools.com/xml/xml_whatis.asp
What is XML Parser?
An XML parser is a parser that is designed to read XML and create a way for programs to use XML. There are different types, and each has its advantages. Unless a program simply and blindly copies the whole XML file as a unit, every program must implement or call on an XML parser.
Reference: http://www.stylusstudio.com/xml/parser.html
What is Denial of Service Attack?
A Denial-of-Service (DoS) attack is an attack meant to shut down a machine or network, making it inaccessible to its intended users. DoS attacks accomplish this by flooding the target with traffic or sending it information that triggers a crash. In both instances, the DoS attack deprives legitimate users (i.e. employees, members, or account holders) of the service or resource they expected.
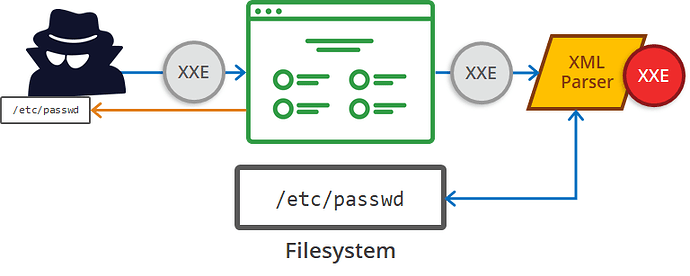
What is XML External Entity?
An XML External Entity attack is a type of attack against an application that parses XML input. This attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser. This attack may lead to the disclosure of confidential data, denial of service, server-side request forgery, port scanning from the perspective of the machine where the parser is located, and other system impacts.
To learn it from scratch Here is the best article for learning: https://www.acunetix.com/blog/articles/xml-external-entity-xxe-vulnerabilities/
I also refer this e-book to learn XML based attacks: https://www.owasp.org/images/5/58/XML_Based_Attacks_-_OWASP.pdf
Today we will see how an attacker can perform DoS attack through XML External Entity. There is an attack called “Billion Laugh Attacks”, as the name suggests there is something that will generate billions of request or billion of smiles ![]()
How does Billion LAUGH Attack work?
The example attack consists of defining 10 entities, each defined as consisting of 10 of the previous entity, with the document consisting of a single instance of the largest entity, which expands to one billion copies of the first entity.
In the most frequently cited example, the first entity is the string “lol” , hence the name “billion laughs” . At the time this vulnerability was first reported, the computer memory used by a billion instances of the string “lol” would likely exceed that available to the process parsing the XML.
While the original form of the attack was aimed specifically at XML parsers, the term may be applicable to similar subjects as well.
Defenses against this kind of attack include capping the memory allocated in an individual parser if the loss of the document is acceptable, or treating entities symbolically and expanding them lazily only when (and to the extent) their content is to be used.
Code example:
<?xml version="1.0"?>
<!DOCTYPE lolz [
<!ENTITY lol "lol">
<!ELEMENT lolz (#PCDATA)>
<!ENTITY lol1 "&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;">
<!ENTITY lol2 "&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;">
<!ENTITY lol3 "&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;">
<!ENTITY lol4 "&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;">
<!ENTITY lol5 "&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;">
<!ENTITY lol6 "&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;">
<!ENTITY lol7 "&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;">
<!ENTITY lol8 "&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;">
<!ENTITY lol9 "&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;">
]>
<lolz>&lol9;</lolz>
When an XML parser loads this document, it seems that it includes one root element, “lolz”, that contains the text “&lol9;”. However, “&lol9;” is a defined entity that expands to a string containing ten “&lol8;” strings. Each “&lol8;” string is a defined entity that expands to ten “&lol7;” strings, and so on. After all the entity expansions have been processed, this small (< 1 KB) block of XML will actually contain 109 = a billion “lol”s , taking up almost 3 gigabytes of memory.
How I discovered this vulnerability?
As usual, I am bound to disclose the website name because it was a private program, So let’s assume https://redacted.com
https://redacted.com was a SOAP-based application which transmit data in XML. Although there are several XML based attacks I was looking for XXE.
The application has file upload functionality where you can upload a file with extension jpg, png, SVG (SVG was allowed and XML code process in SVG)
I upload an SVG file containing XXE payload and tried different techniques to get the file system but the application was quite secure and XML parser was properly configured. I also tried OOB-XXE and tried almost all XML parser bypasses such as Bypass through CDATA, through parameter entity and through PHP Protocol Wrappers, etc. but no luck!!!
Then I tried for DoS attack and upload an SVG file containing “Billion LAUGH Attack” payload and after upload when I open the file billions of entities processed and server shocked ![]()
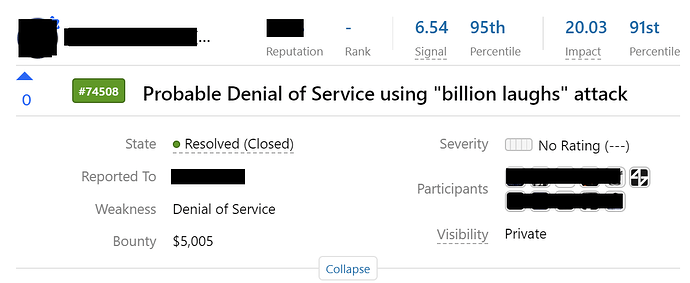
I reported the vulnerability but unfortunately, it was a duplicate and the researcher who reports this vulnerability first got the bounty of $5,005.
Yes, it HURTS !!!
But no problem, it’s part of the game.
Recommendations:
- Block SVG,XML and Html, etc. file extensions
- Don’t allow DTDs
- Don’t expand entities
- Don’t resolve externals
- Limit parse depth
- Limit total input size
- Limit parse time
- Favor a SAX or iterparse-like parser for potential large data
- Validate and properly quote arguments to XSL transformations and XPath queries
- Don’t use XPath expression from untrusted sources
- Don’t apply XSL transformations that come untrusted sources
- Completely disable Document Type Definitions (DTDs)
I hope you guys learned something new from this thread. Thanks for reading !!!
Source: medium

 !
!