Encrypted message or informations can be inserted in document file. You know, some organisations is send informations that encrypted in document file. Because, with that competitor is not easy to intercept the informations. If you work as a digital forensic you need to know how to find message or information that hidden in document file. A Metadata viewer tool that can help you do that is “FOCA (Fingerprinting Organizations with Collected Archives)“ , this tool will analyze a wide variety of documents, with the most common being Microsoft Office , Open Office , or PDF files, although it also analyses Adobe InDesign or SVG files, for instance.
Description
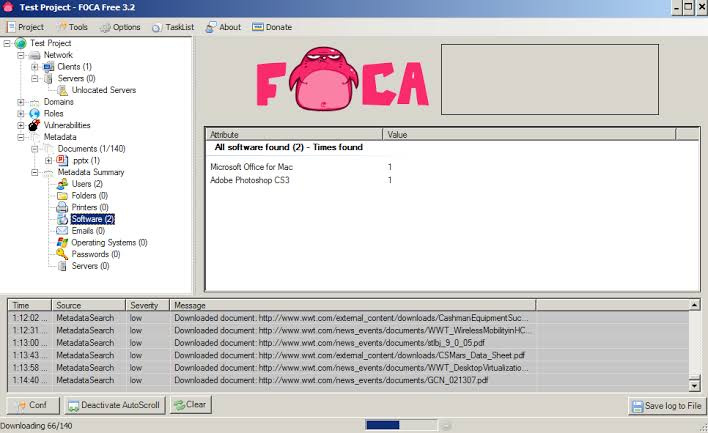
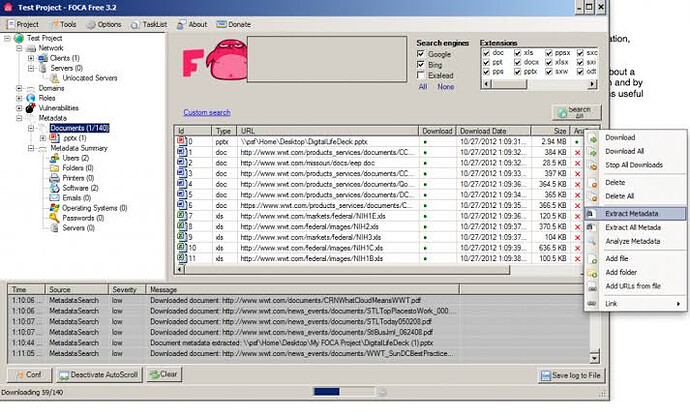
FOCA is a tool used mainly to find metadata and hidden information in the documents it scans . These documents may be on web pages, and can be downloaded and analysed with FOCA.
It is capable of analysing a wide variety of documents, with the most common being Microsoft Office , Open Office , or PDF files, although it also analyses Adobe InDesign or SVG files, for instance.
These documents are searched for using three possible search engines: Google , Bing , and DuckDuckGo . The sum of the results from the three engines amounts to a lot of documents. It is also possible to add local files to extract the EXIF information from graphic files, and a complete analysis of the information discovered through the URL is conducted even before downloading the file.
Functionality
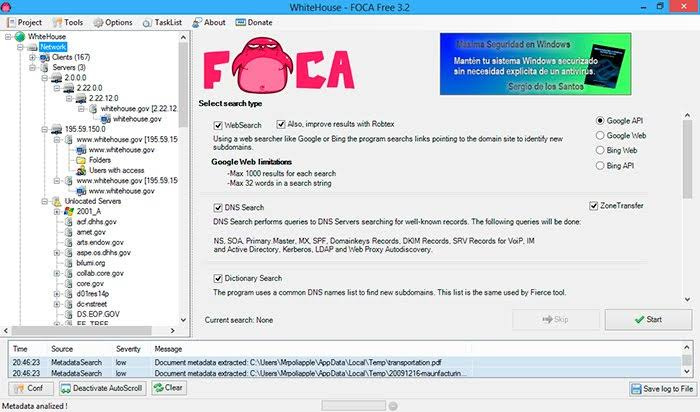
FOCA includes a server discovery module, whose purpose is to automate the servers search process using recursively interconnected routines. The techniques used to this end are:
Web Search
Searches for hosts and domain names through URLs associated to the main domain. Each link is analyzed to extract from it new host and domain names.
DNS Search
Each domain is checked to ascertain which are the host names configured in NS, MX, and SPF servers to discover new host and domain names.
IP resolution
Each host name is resolved by comparison to the DNS to obtain the IP address associated to this server name. To perform this task as accurately as possible, the analysis is carried out against a DNS that is internal to the organization.
PTR Scanning
To find more servers in the same segment of a determined address, IP FOCA executes a PTR logs scan.
Bing IP
For each IP address discovered, a search process is launched for new domain names associated to that IP address.
Common names
This module is designed to carry out dictionary attacks against the DNS. It uses a text file containing a list of common host names such as ftp, pc01, pc02, intranet, extranet, internal, test, etc.
DNS Prediction
Used for those environments where a machine name has been discovered that is reason to suspect that a pattern is used in the naming system.
Robtex
The Robtex service is one of many services available on the Internet to analyze IP addresses and domain names. FOCA uses it in its attempt to discover new domains by searching the information available in Robtext on the latter.
Features
FOCA began as a metadata analysis tool to draw a network based on said metadata. Today, it has become a reference in the computer security sector due to the many options it includes. Thanks to the aforementioned FOCA options, it is possible to undertake multiple attacks and analysis techniques such as:
- Metadata extraction.
- Network analysis.
- DNS Snooping.
- Search for common files.
- Juicy files.
- Proxies search.
- Technologies identification.
- Fingerprinting.
- Leaks.
- Backups search.
- Error forcing.
- Open directories search.
In addition, FOCA has a series of plugins to increase the functionality or number of attacks that can be carried out to elements obtained during the analysis that may be downloaded from the FOCA Market .
Releases
Check here our latest releases.
Requisites
To run the solution locally the system will need:
- Microsoft Windows (64 bits). Versions 7, 8, 8.1 and 10.
- Microsoft .NET Framework 4.7.1 .
- Microsoft Visual C++ 2010 x64 or greater.
- An instance of SQL Server 2014 or greater.
Notes
- When starting the app the system will check if there is a SQL Server instance available. If none is found, the system will prompt a window for introducing a connection string.
 !
!