OWASP Amass Project
In-depth DNS Enumeration, Attack Surface Mapping and External Asset Discovery!
The OWASP Amass Project has developed a tool to help information security professionals perform network mapping of attack surfaces and perform external asset discovery using open source information gathering and active reconnaissance techniques.
Description
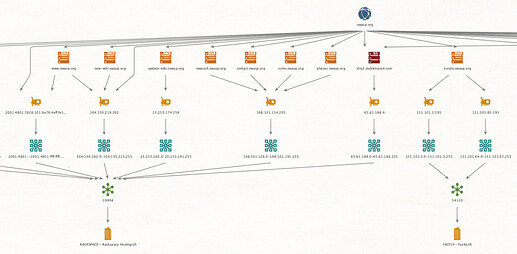
The OWASP Amass project is focused on DNS enumeration and network infrastructure mapping techniques. These techniques include: obtaining subdomain names by scraping web pages, accessing web APIs, querying public databases, recursive brute forcing, crawling web archives, permuting/altering DNS names, reverse DNS sweeping, and querying ASNs and netblocks associated with IP addresses. The information collected during an enumeration is used to build a graph database that maps an organization’s presence on the Internet.
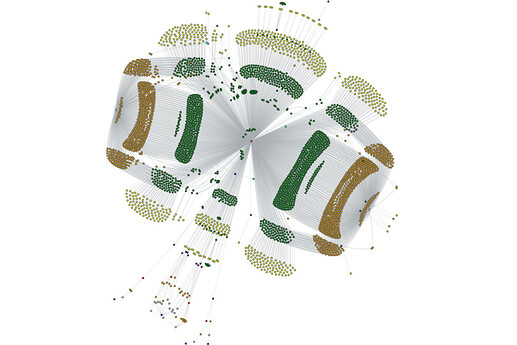
When the enumeration is complete, an Amass tool is capable of converting the results into several different formats accepted by popular network graph visualization engines. This aids analysts and infosec experts attempting to quickly identify network layout and external networks being utilized by the target organization.
The software is implemented in the Go programming language, and is portable across popular operating systems such as Windows, Linux, MacOS, FreeBSD, etc. The command-line tools can be obtained via several mechanisms described on the installation page, such as through a Go development environment, the release binaries, the Snap package manager for Linux systems and various packages maintained by others.
Information Gathering Techniques Used:
- DNS: Basic enumeration, Brute forcing (optional), Reverse DNS sweeping, Subdomain name alterations/permutations, Zone transfers (optional)
- Scraping: Ask, Baidu, Bing, DNSDumpster, DNSTable, Dogpile, Exalead, Google, HackerOne, IPv4Info, Netcraft, PTRArchive, Riddler, SiteDossier, ViewDNS, Yahoo
- Certificates: Active pulls (optional), Censys, CertSpotter, Crtsh, Entrust, GoogleCT
- APIs: AlienVault, BinaryEdge, BufferOver, CIRCL, CommonCrawl, DNSDB, GitHub, HackerTarget, Mnemonic, NetworksDB, PassiveTotal, Pastebin, RADb, Robtex, SecurityTrails, ShadowServer, Shodan, Spyse (CertDB & FindSubdomains), Sublist3rAPI, TeamCymru, ThreatCrowd, Twitter, Umbrella, URLScan, VirusTotal, WhoisXML
- Web Archives: ArchiveIt, ArchiveToday, Arquivo, LoCArchive, OpenUKArchive, UKGovArchive, Wayback
Documentation
Use the Installation Guide to get started.
Go to the User’s Guide for additional information.
Usage
The amass tool and all the subcommands show options using the ‘-h’ and ‘-help’ flags:
amass -help
The most basic use of the tool for subdomain enumeration:
amass enum -d example.com
Typical parameters for DNS enumeration:
$ amass enum -v -src -ip -brute -min-for-recursive 2 -d example.com
[Google] www.example.com
[VirusTotal] ns.example.com
...
Command-line Usage Information
The amass tool has several subcommands shown below for handling your Internet exposure investigation.
| Subcommand | Description |
|---|---|
| intel | Collect open source intelligence for investigation of the target organization |
| enum | Perform DNS enumeration and network mapping of systems exposed to the Internet |
| viz | Generate visualizations of enumerations for exploratory analysis |
| track | Compare results of enumerations against common target organizations |
| db | Manage the graph databases storing the enumeration results |
Read the User Guide For more information.
Importing Amass Results into Maltego
Convert the Amass data into a Maltego graph table CSV file:
amass viz -maltego
Import the CSV file with the correct Connectivity Table settings:
All the Amass findings will be brought into your Maltego Graph:

 !
!