RapidScan - The Multi-Tool Web Vulnerability Scanner
RapidScan - The Multi-Tool Web Vulnerability Scanner
Evolution:
It is quite a fuss for a pentester to perform binge-tool-scanning ( running security scanning tools one after the other ) sans automation. Unless you are a pro at automating stuff, it is a herculean task to perform binge-scan for each and every engagement. The ultimate goal of this program is to solve this problem through automation; viz. running multiple scanning tools to discover vulnerabilities, effectively judge false-positives, collectively correlate results and saves precious time ; all these under one roof.
Enter RapidScan .
Features
- one-step installation .
- executes a multitude of security scanning tools , does other custom coded checks and prints the results spontaneously .
- some of the tools include
nmap, dnsrecon, wafw00f, uniscan, sslyze, fierce, lbd, theharvester, dnswalk, golismeroetc executes under one entity. - saves a lot of time, indeed a lot time! .
- checks for same vulnerabilities with multiple tools to help you zero-in on false positives effectively.
- legends to help you understand which tests may take longer time, so you can
Ctrl+Cto skip if needed. - association with OWASP Top 10 2017 on the list of vulnerabilities discovered. ( under development )
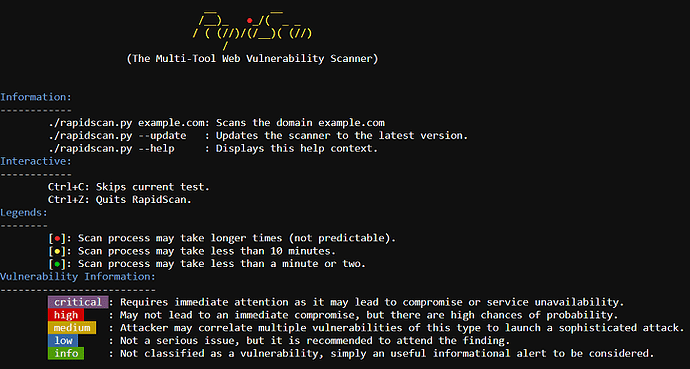
- critical, high, medium, low and informational classification of vulnerabilities.
- vulnerability definitions guides you what the vulnerability actually is and the threat it can pose. (
under development) - remediations tells you how to plug/fix the found vulnerability. (
under development) - executive summary gives you an overall context of the scan performed with critical, high, low and informational issues discovered. ( under development )
- artificial intelligence to deploy tools automatically depending upon the issues found. for eg; automates the launch of
wpscanandplecosttools when a wordpress installation is found. ( under development ) - detailed comprehensive report in a portable document format (*.pdf) with complete details of the scans and tools used. ( under development )
FYI:
- program is still under development, works and currently supports 80 vulnerability tests.
- parallel processing is not yet implemented, may be coded as more tests gets introduced.
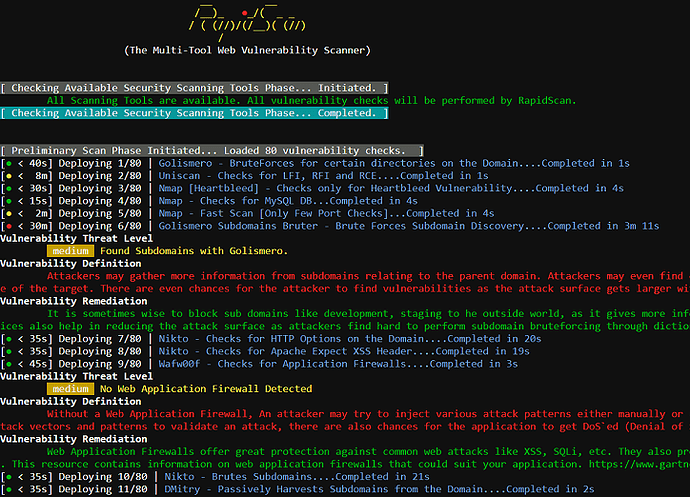
Vulnerability Checks
 DNS/HTTP Load Balancers & Web Application Firewalls.
DNS/HTTP Load Balancers & Web Application Firewalls. Checks for Joomla, WordPress and Drupal
Checks for Joomla, WordPress and Drupal SSL related Vulnerabilities ( HEARTBLEED, FREAK, POODLE, CCS Injection, LOGJAM, OCSP Stapling ).
SSL related Vulnerabilities ( HEARTBLEED, FREAK, POODLE, CCS Injection, LOGJAM, OCSP Stapling ). Commonly Opened Ports.
Commonly Opened Ports. DNS Zone Transfers using multiple tools ( Fierce, DNSWalk, DNSRecon, DNSEnum ).
DNS Zone Transfers using multiple tools ( Fierce, DNSWalk, DNSRecon, DNSEnum ). Sub-Domains Brute Forcing.
Sub-Domains Brute Forcing. Open Directory/File Brute Forcing.
Open Directory/File Brute Forcing. Shallow XSS, SQLi and BSQLi Banners.
Shallow XSS, SQLi and BSQLi Banners. Slow-Loris DoS Attack, LFI ( Local File Inclusion ), RFI ( Remote File Inclusion ) & RCE ( Remote Code Execution ).
Slow-Loris DoS Attack, LFI ( Local File Inclusion ), RFI ( Remote File Inclusion ) & RCE ( Remote Code Execution ).- & more coming up…
Requirements
- Python 2.7
- Kali OS ( Preferred , as it is shipped with almost all the tools )
For other OS flavours, working on a docker support. Hang on.
Usage
Download the script and give executable permissions
wget -O rapidscan.py https://raw.githubusercontent.com/skavngr/rapidscan/master/rapidscan.py && chmod +x rapidscan.py
With docker
To run a scan for example.com the command below has to be run. After completion reports can be found in the current path under reports .
docker run -t --rm -v $(pwd)/reports:/reports kanolato/rapidscan example.com
It is also possible to see rapidscan options running: docker run -t --rm kanolato/rapidscan