There is a tool built into Kali that can shed light on the strategies people use to create their passwords. This tool was developed by Robin Wood of ceWL fame.
Of course, I hope it goes without saying that this does not apply on every password and user, but remember we only have to crack one password to take down the entire network.
Step #1: pipal Help
Let’s begin by taking a look at the pipal help screen.
kali > pipal -h
As you can see, the pipal syntax is simple. In most cases, we only need to invoke pipal with the number of top results we want to view and the filename of the containing the passwords.
pipal Syntax:
pipal <-t number of top results>
Step #2: Test pipal on sample password lists
One is from a password dump from Comcast users (Comcast is the largest cable TV and Internet provider in the US) from a few years back. In this file you will find nearly 600,000 unencrypted passwords. Let’s start by using this list to see how people are creating their passwords.
Make certain to download this list to your Kali system. I have downloaded this list to a flash drive and then connected the flash drive to my Kali VM. To bein the password analysis, simply enter;
kali > pipal -t 10 “comcast passwords.txt”
As you can see above, pipal took just 30 seconds to analyze this password file. It then displayed the top 10 passwords indicating that “password” was the most common, “bluebird” was 2, and “12345678” was third. Also, note that the 10th most common password was “comcast1”. It has been my observation that people often use the name of the service in their passwords usually followed by a number. This makes it easier for them to remember and easier to crack.
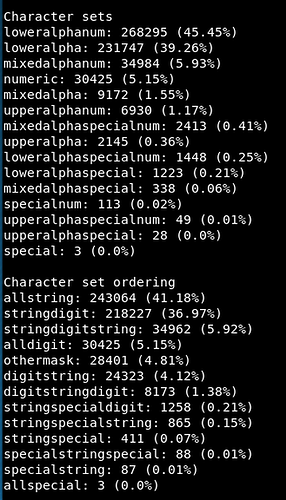
If we scroll down the results, we can find data on the character sets used. On this list, 45% of the passwords use a lower case alphabetic characters and numbers and 39% use just lower case alphabetic characters.