“A new report published today reveals that Iran’s government-backed hacking units have made a top priority last year to exploit VPN bugs as soon as they became public in order to infiltrate and plant backdoors in companies all over the world,” writes ZDNet:
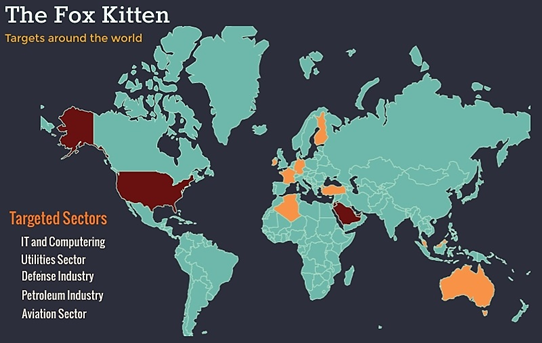
According to a report from Israeli cyber-security firm ClearSky, Iranian hackers have targeted companies “from the IT, Telecommunication, Oil and Gas, Aviation, Government, and Security sectors.” The report comes to dispel the notion that Iranian hackers are not sophisticated, and less talented than their Russian, Chinese, or North Korean counterparts. ClearSky says that “Iranian APT groups have developed good technical offensive capabilities and are able to exploit 1-day vulnerabilities in relatively short periods of time.” [ATP stands for “advanced persistent threat” and is often used to describe nation-state backed cyberattackers.]
In some instances, ClearSky says it observed Iranian groups exploiting VPN flaws within hours after the bugs have been publicly disclosed…
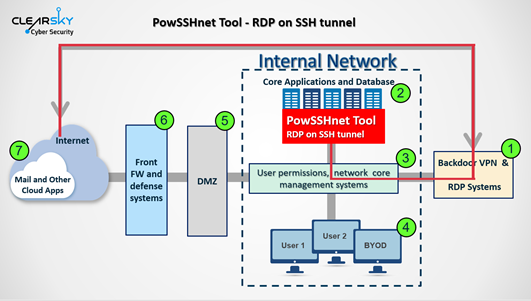
According to the ClearSky report, the purpose of these attacks is to breach enterprise networks, move laterally throughout their internal systems, and plant backdoors to exploit at a later date.