What is Cyber Security ?
Cyber security is a form of protecting servers, local networks, user data from cyber attacks. Cyber attacks are intended to steal login credentials, users data including financial information and breaking other businesses. Cyber security are intended to protect users privacy, data, financial information and other information which can go to wrong hands. Now days implementing cyber security is the greatest challenge in some organisations. Because there are some companies or organisations which are not still ready to understand about Cyber security implementations.
Cyber Security Topics
Leaving Backdoor Open
Leaving Backdoor Open
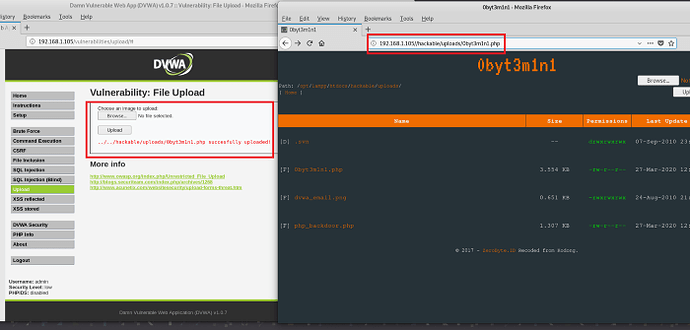
Backdoors which are the most common loophole what every cyber criminals tries to find out. Backdoors are generally refer to website flaws. Most of the websites stores users information, using old scripts or not using secure coding techniques could led cyber criminals to attack on such sites. Having inappropriate servers configurations could also give access to backdoor. Mostly criminals uses takes advantage of such bad configuration and downloads all credentials. There are many automation tools which are designed to accessing backdoors. Many open source frameworks are designed to access backdoors of any website. Depending on the language on which website has developed. For example — on php, there are many backdoors which are used access website local servers. You can easily find such backdoors on github. Below screenshot shows that how small php script of backdoor has accessed website server.
php backdoors example
For testing we have used DVWA . Damm Vulnerability Web Application. Simply download and open the iso using virtualbox.
Open its images upload page and upload backdoor. For accessing backdoor. Open browser type http://192.168.1.105/hackable/uploads/backdoor_name.php
Simple PHP backdoo r
Above is the example that how backdoor can be used to access website server. Normally, backdoors are accessed by cyber criminals to steal all files and important directories. Above shows website upload directory with files and its permission. To avoid such backdoor attacks, regular cyber security audits are required which analyses and tells where security can be implemented.
Downloading Unverified Content From Any Website
Unverified Software’s
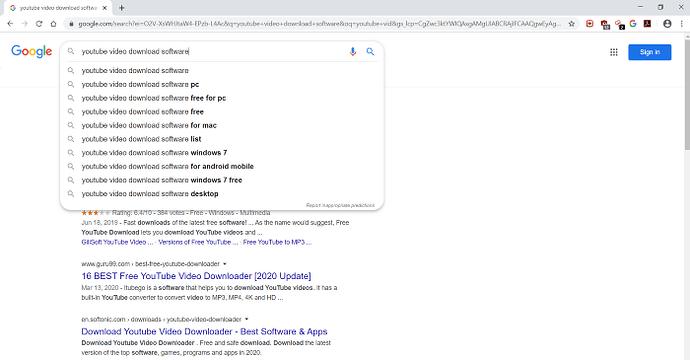
Most of internet users makes such mistake. Using any software for their work without verifying. While searching for any desired work to be done, every user try to search for any software which can handle their task. Every software available on the internet is not what you are looking for. Most of them contains malware’s, viruses which can infect your computer. There are ample amount of malware’s which can infect your computer. Malware’s are designed to trick victim’s to install them in their computer. Some malware are automate bots designed complete an task in automated way without notifying in any manner to victim. For example — YouTube is very common video streaming platform. There are many users who always tries to download videos from YouTube. While searching on the internet, you will found many ways to download video from YouTube. Below screenshot that how users are keen to download YouTube content.
Using Unverified Software
Above screenshot shows the popular google searches for downloading YouTube videos. There are many malware’s rolling on the internet defining themselves as YouTube video downloader. Users download and installs such malware’s without being aware. From that point cyber criminals start their another activities from stealing personal financial information to getting their password hashes. To avoid such malware attacks users should always use appropriate way of downloading videos through YouTube. YouTube gives an option of SAVING videos.
Sharing Your Social Media ID with Anyone Or Accepting Request Of Unknown’s
Social Media Fake Followers
Every person loves to get popular, In a short period of time everyone needs popularity. And now days Social Media has become the main stream for everyone. Every person which is using Social Media platforms become so influenced that their first priority is to become popular on such platforms. For gathering or creating an follower base on social media. You need to be very specific about your thoughts what you speak. What type of audience are you actually gathering ? Social media do come with variety of audience. Some build their own audience but most of them are very specific. For Social media popularity, people are using shortcut methods. Accepting request of unknown, creating fake accounts with different names, Using bots for increasing followers and various methods which can put their privacy at risk. Because accepting request from unknown could led to cyber stalking or other cyber crimes. Below screenshot shows the perfect example of this topic.
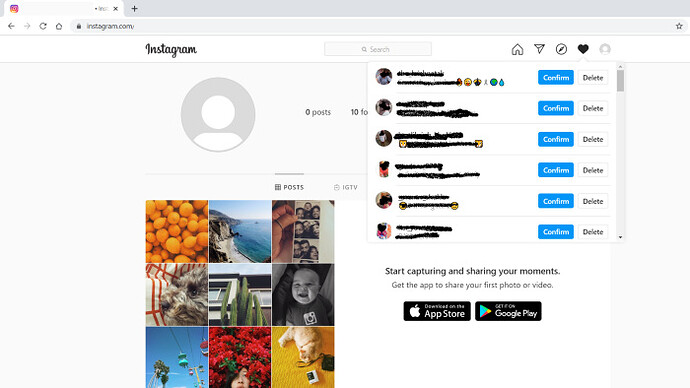
For example — We have created account on Instagram. After creating account on Instagram, we have started receiving request from unknown person. That we even don’t know. Instagram is very popular platform for sharing photos, memories. But there are some users who has started spamming on Instagram. Below screenshot shows request from unknown person. For security reasons we have hidden all the names and pictures.
Instagram — Receiving Unknown Request
Above scenario shows that after creating account how unknown request started receiving ? To avoid such spamming, do not accept request from unknown. It might be trap for you. Do not click on any link, claiming to increase your followers in short period of time. This may even block your account from Instagram or any social media platform.
Hackers Can Come From Anywhere
Hackers Can Come From Anywhere
When hacker has decided to enter into your servers. Hacker will definitely find a way to hijack into servers. Normally, every hacker starts by information gathering. Depending on the information what hacker has gathered. Then he/she prepares for the next phases. There are many methods in which hackers tries to hijack. But most common method hackers tries to is Social Engineering. Still an old but very effective Social Engineering. Social Engineering is the most common method which every hacker uses to attack. According to hackers perspective, such method makes there attack more easy. Because victim itself clicks on such malicious links. Social engineering attacks are mostly used methods to hijack any user. Coming future of cyber attacks relies mostly on social engineering. Social engineering is a way of cloning original web page into malicious web page. User interface in which every end user rely on. Generally most users always remember web pages by just looking its on user interface. Why Social Engineering attacks are still active ? Because Human stupidity can’t be patched with piece of code. In humans, consciousness define there psychology behavior that how humans are aware of sharing their credentials with any web site. There are many methods which are used in social engineering attacks. Some are very common methods and still very widely used.
Social Media Example
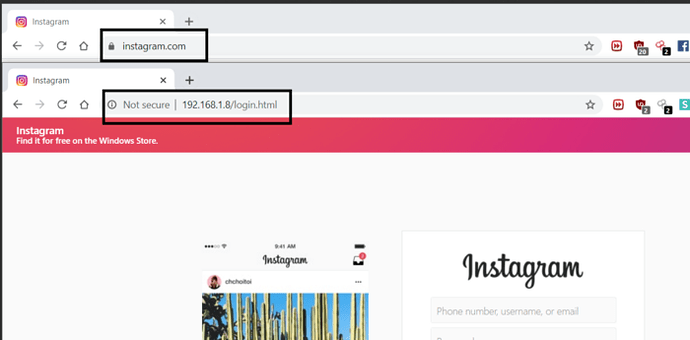
Here we have created fake link of Instagram. a very popular photo sharing site. Below you will see difference between fake link and original one.

Social Engineering
Above shows the fake link and the original Instagram.
Fake Link and Original Link
Above scenario relates to social engineering techniques. That how hackers uses various methods for hijacking. To avoid such attacks, whenever you found any link to be suspicious. You can search such links in virustotal.com or you can use online link expander for finding links are suspicious or not.
Cyber Security Tips From Cyber Attacks
Cyber Security Tips
Always update your operating system. Either it is Windows or it is Mac. Update your operating systems to latest patches.
Do not use public Wifi for financial transactions. Many users use public Wifi which can cause to session hijacking.
Use a good anti-virus. Now days you will find many good anti-virus in the market.
Do not open or click on suspicious links or install any software. If you want to open or install any software. Use Virtualization methods for using such software’s or links.
Do not open email attachments from unknown senders. Marketing tips, increase your money, jobs fake portals, chat with new friends. Such methods are used to spread malware.
In last we would say STAY SAFE, DO NOT CLICK ON ANY UNKNOWN LINK OR INSTALL ANY SOFTWARE (Source: medium)
Happy learning!