Open-source intelligence or OSINT is a potent technique, and it may give so much of valuable information, if implemented accurately with the right strategy and proper tools. In this text, I’ll show you the way a hacker can get passwords of hundreds of email addresses with out attacking the webserver or with out using another hacking technique; however, just using the power of OSINT.
You can implement all the techniques discussed on this article manually; nonetheless, to improve the operation and to maximize the result, we’ll utilize Maltego together with a web service called Have I been Pwned?
Blackhat hackers usually post and publish data after hacking a webserver; for instance, they dumped Linkedin hacked accounts and others. Let’s just fetch all this valuable information smartly.
Tools used on this article:
- theHarvester
- Maltego
- Have I been Pawned
I’ve discussed the configuration of Maltego with Have I been Pawned before; so, let’s just skip this part.
Step 1: Getting email addresses using the email harvesting tool, theHarvester
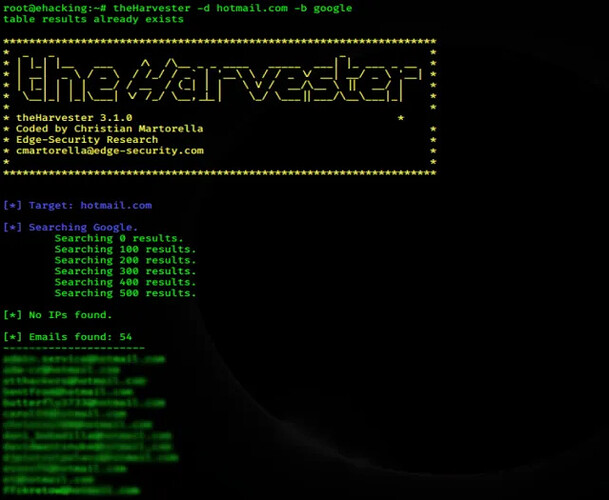
As a place to begin, let’s search the google for email address using theHarvester tool.
# theHarvester -d hotmail.com -b google
You can use any organization’s domain or another particular target, when you’ve got. A basic search gave us lots of information (54 email addresses) to begin. Let’s copy a few of them into the CSV file and import them into Maltego for further analysis. The reason for copying a few is the ease of maintaining the operation because, in the Maltego, you will note an enormous connection of only a few email addresses.
Step 2: Importing the Data into Maltego for further analysis
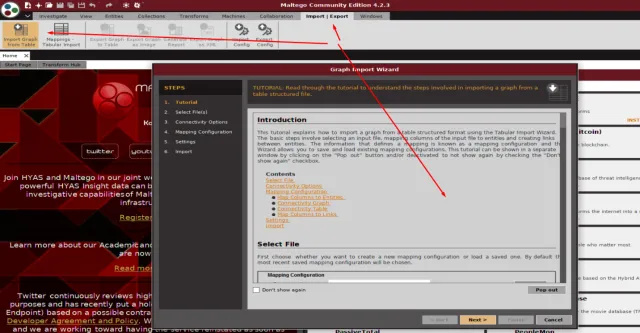
I’m selecting the manual option, so no previous connection.
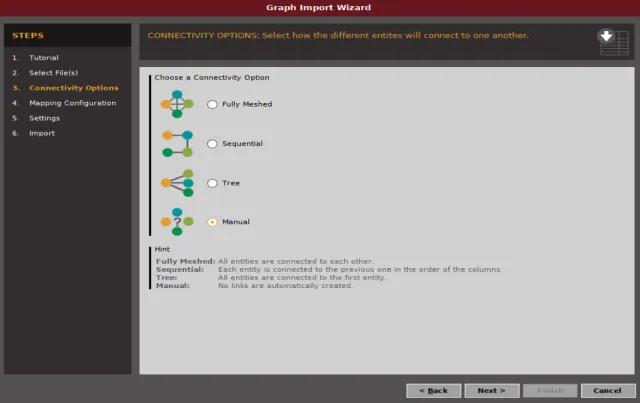
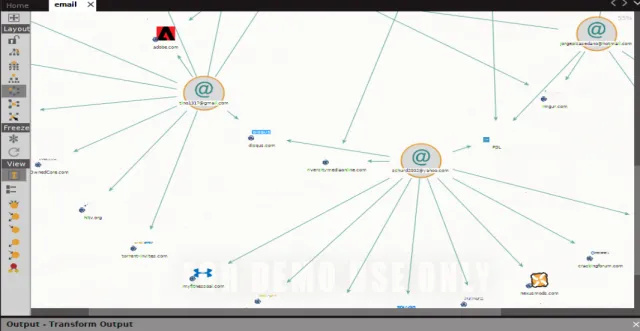
Step 3: Find the breaches where the target email addresses appeared
Select all the email addresses, since I’ve only imported 11 of them, and run the Have I been Pawned rework to check whether the target email addresses been hacked before or not. If it isn’t the part of any breach, then just drop it; it’s of no use.
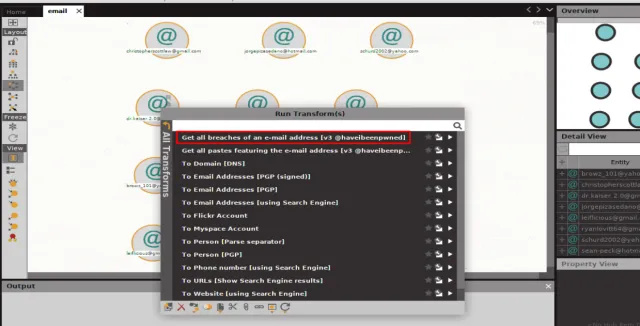
There we will see so many email addresses appeared in lots of breaches. I’ve dropped some, two email addresses out of 11 because they didn’t appear in any breach. Remember that we’re just gathering information, not hacking or directly attacking any server; so, if an email was not acquired hacked before, it received’t be useful for us.
Step 4: Find the Plain Text Passwords of the Hacked Email addresses
The most common follow in the {industry} is to paste or dump the hacked email addresses details into Pastebin; it’s a web site where you possibly can store text for some particular time. This time, let’s execute the second rework:
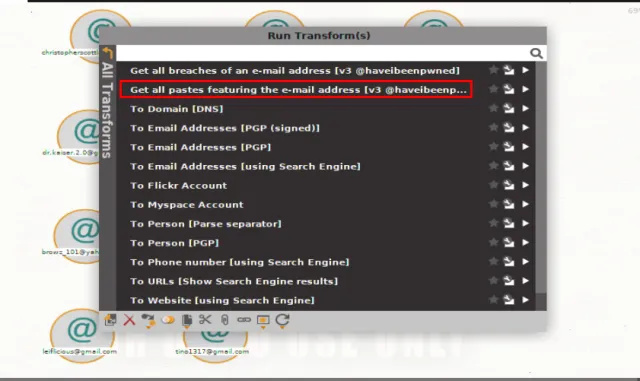
Each email addresses appearing in lots of Pastebin text.

Open any Pastebin URL and analyze the data.
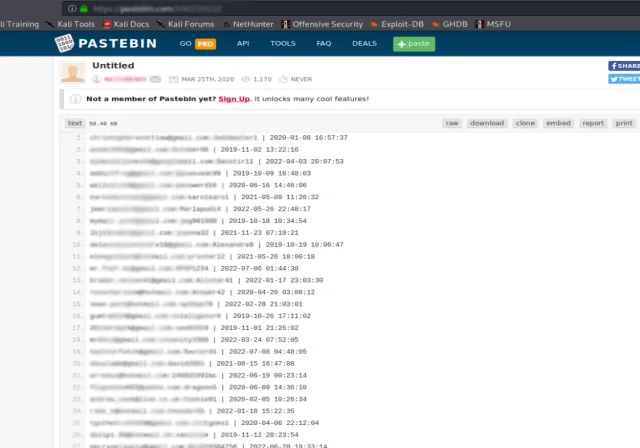
Wahoo, very recent data with the plain text password, email account, and the expiry date of a specific subscription, the blackhat guys use this information to ask a ransom. A common man doesn’t know that somebody published his confidential information online.
Step 5: Try to report it to the authority
Being a responsible cyber security professional, it is best to inform the authority or no less than make it possible for the hacked web site or service ought to notify about changing the password to all its members.
As you possibly can see, the power of open-source intelligence gathering, and we now have started with only a random email acquired from the Google search. Imagine a malicious person with evil intent can do investigation against any particular target, let say a company to check the employee details and attainable passwords. And as soon as the evil person acquired the password, he can further dig into the organization confidential information, or he can send his malware and backdoor to hack the complete organization. We have covered the same story; it is best to this out.
Source: securityloops
I hope you like the tutorial folks!