Ransomware gangs are getting more aggressive these days about pursuing payments and have begun stealing and threatening to leak sensitive documents if victims don’t pay the requested ransom demand.
Starting with late 2019 and early 2020, the operators of several ransomware strains have begun adopting a new tactic.
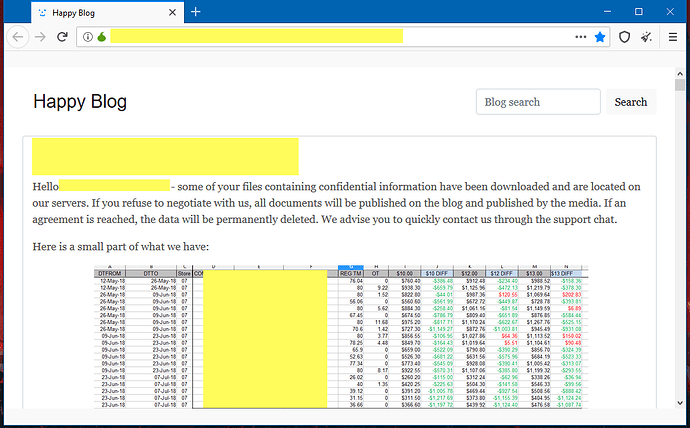
In an attempt to put additional pressure on hacked companies to pay ransom demands, several ransomware groups have also begun stealing data from their networks before encrypting it.
If the victim – usually a large company – refuses to pay, the ransomware gangs threaten to leak the information online, on so-called “leak sites” and then tip journalists about the company’s security incident.
Companies who may try to keep the incident under wraps, or who may not want intellectual property leaked online, where competitors could get, will usually cave in and pay the ransom demand.
While initially the tactic was pioneered by the Maze ransomware gang in December 2019, it is now becoming a widespread practice among other groups as well.
There’s now COVID-19 malware that will wipe your PC | Six suspected drug dealers went free after police lost evidence in ransomware attack | 30 years of ransomware: How one bizarre attack laid the foundations for the malware taking over the world | TechRepublic: Why SMBs are especially vulnerable to attacks
At the time of writing, ZDNet has identified nine ransomware operations that are currently running or have maintained a “leak site,” either on the dark web, or the public internet.
Below is a list of all ransomware “leak sites,” in alphabetical order, which we’ll maintain going forward, as an index of all groups that engage in this tactic. We will not be linking to any of these sites, nor will we be listing any past or present victims. This lists exists solely for the purpose of letting victim companies know that in the case of an infection with any of the ransomware strains listed below that they should treat the incident as a classic data breach where data has been exfiltrated and has reached a third-party’s hands, rather than just a ransomware were data was merely encrypted but never left a victim’s network.
Ako
CLOP
DoppelPaymer
Maze
Mespinoza (Pysa)
Nefilim
Nemty
NetWalker
RagnarLocker
REvil (Sodinokibi)
Sekhmet
Snatch
The Snatch ransomware gang’s “leak site” has been down for weeks. It is unclear if the group has abandoned the leaking files from infected hosts, or has moved it to a secret new URL.
Source: Zdnet